What is the Zero Trust Model?
If you’re alone in your house with the doors and windows locked you can be certain that your silverware is safe barring a burglar breaking in but if you’ve got good locks you can probably relax. You have your castle and your physical defenses are, in effect, your moat. Now add in your spouse. The chance of your silverware going missing has just statistically increased; not by much perhaps but, well, you just never know. Now add in your kids and your mother in the granny flat. The chance of someone purloining your valuables just got another bump up and, again, hopefully not by much although the chance is now definitely not zero. Now your siblings and in-laws turn up along with your old friend from college who needs somewhere to crash and then the plumber arrives to fix the blocked drains and …
When it was just you alone, you could trust that your valuables were secure but as the internal population increases and the traffic crossing your moat increases, your confidence in your security would drop accordingly.
Defending the Enterprise
The same kind of problem also applies in enterprise IT environments and until a decade ago, the castle-and-moat model—that is, the assumption that what’s inside the moat and castle is safe—was the dominant strategy. But as the cost of enterprise security continued to grow year-on-year, driven by the increasing frequency and cost of data breaches, a new approach to enterprise security became necessary. Enter the Zero Trust model.
In 2010, John Kindervag, a principal analyst at Forrester Research Inc., created the Zero Trust model, which argues that without verification, you should never trust network connections, whether from inside or outside the organization’s envelope. This makes a sense because as hacking techniques have become more sophisticated and effective—particularly phishing and spear phishing—bad guys often gain internal access, which then short-circuits moat-and-castle defenses. Moreover, the migration to a Polynimbus cloud infrastructure involves extending the enterprise IT footprint in new ways so the need for in-depth security is more pressing than ever.
How to Build Zero Trust Security Defenses
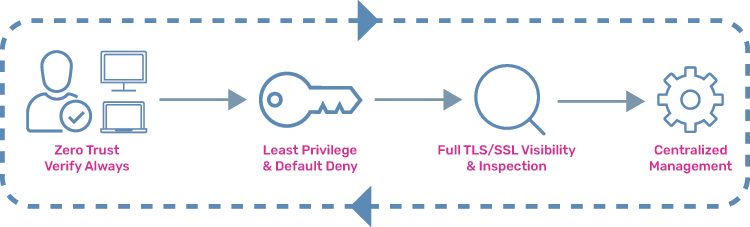
The first line of a Zero Trust security strategy is to know, which communications endpoints are secure and who or what is active at each endpoint. This requires multifactor authentication, encryption, analytics, file system permissions, integrated access management, and minimal access policies. But the most crucial component of the Zero Trust model is having the ability to analyze content transferred over secured and unsecured network connections.
This requires application delivery controllers with TLS/SSL decryption and TLS/SSL inspection capability so you can detect malware and sensitive data transfers, for example, personally identifiable information or PII, and block and report them. The Zero Trust model is the most effective security strategy for on-premises and multi-cloud networking security.
How A10 Can Help
A10 Networks’ industry-leading Thunder® Application Delivery Controller (ADC), available in both hardware and software form factors, provides deep packet inspection and filtering as well as centralized management, SSL offloading, load balancing, and traffic-shaping making A10 Networks the most cost-effective core of a Zero Trust security strategy.
Zero Trust Model Articles and Assets of Interest
- Zero Trust Model is Meaningless Without TLS Inspection
- Select TLS/SSL Decryption Essential for Strong Zero Trust Strategy
- Online Gaming Needs a Zero-Trust DDoS Defense
- Ransomware Attacks Threaten Election Security – and Much More
- Hybrid Cloud Application Delivery in Financial Services
- Zero Trust is Incomplete Without TLS Decryption (White Paper)
- TLS, Compliance and Zero Trust – Protecting Users from Cyberattacks (Webinar)
- Enabling Full Visibility for Zero Trust Networks (Webinar)
