What is Network Security and Who Suffers DDoS Attacks?
Network Security Starts With Having a Well-protected Network
This means keeping intruders out, and continuously scanning for potential breaches, malware and flagging those attempted compromises. One of the biggest threats increasing in popularity is a very specific type of attack called distributed denial of service (DDoS) attacks. These attacks are targeted at your internet servers, including web and database servers, and are designed to flood random traffic so that the servers can’t respond to legitimate users’ queries.
They are very easy to mount, and without the right tools, very hard to prevent. DDoS attacks typically make use of two different cloud-based services that are easily available and for very low cost (less than $100/month in many circumstances). These services offer multiple attack vectors and the ability to target whomever you wish. This puts cloud security and web security both firmly in the spotlight, since lapses in these two areas can make the potential for a DDoS attack more likely, and to potentially weaken your overall network security.
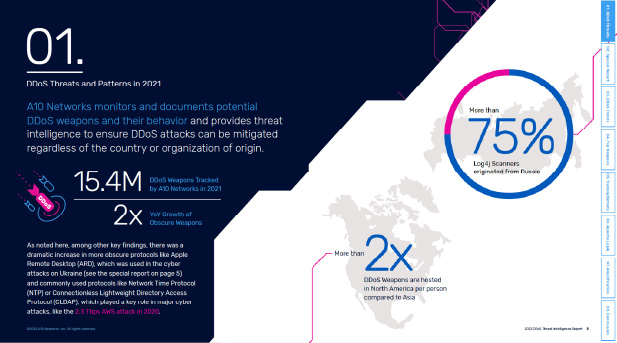
This ease of use is one reason why A10 Networks DDoS Threat Report for 2022 found that more than 15 million unique DDoS weapons were discovered during 2021, almost tripling in size from three years ago. The Russia-Ukraine war brought new instances of state-sponsored DDoS attacks on critical infrastructure and challenges to network security such as utilities and transportation services.
The DDoS attack is assembled from an army of automated bots that is orchestrated by the attacker, often from many thousands of computers located across the world. The distribution of attackers – or computers using a botnet attack vector — makes it harder to stop the attack and also harder to identify the source and identity of the coordinator.
Security researcher Brian Krebs, who has been targeted with hundreds of DDoS attacks beginning in 2016, has documented how these attacks happen.
The typical victims of DDoS attacks are higher-profile organizations such as banks, government agencies, or media companies, but really any business can become a target. By crashing or stopping a web server, they are designed to cost the target business time and money to repair the server and bring it back online.
Trends in DDoS Attacks
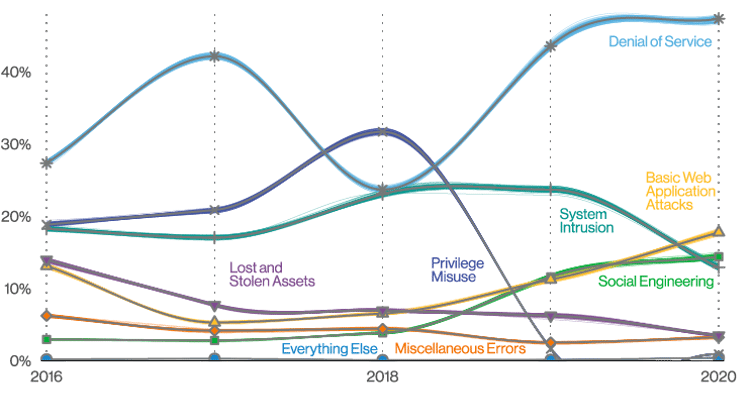
DDoS attacks are not a new phenomenon. The first known attack occurred in 1996 with an early internet provider Panix being taken offline. Since then, DDoS attacks are not only getting more frequent, but their scope is increasing. This is partly due to DDoS attackers getting better at harnessing more and more bandwidth to bring down their targets. The Verizon 2022 Data Breach Report has tracked this trend.
Back in 2013, the median DDoS attack was around 422 Mbps, with a very small number hitting the Gbps mark. Today, the median lasted less than four hours and is around 1.3 Gbps, with several in the terabit range. Verizon found that today’s DDoS infrastructure is far more formalized and repeatable, one of the reasons why its report noted that DDoS attacks have been the most popular method among all malware-based attacks used since 2019.
In November 2021, Microsoft mitigated a DDoS attack targeting an Azure customer with a throughput of 3.45 Tbps — this is believed to be the largest documented DDoS attack. Other notable attacks include these:
- Google in October 2020 tracked to Chinese sources that reached 2.5 Tbps
- Amazon’s Web Services in February 2020 that reached 2.3 Tbps and lasted for three days
- European hosting provider OVH was hit in September 2016 with a seven-day attack that peaked at 1.1 Tbps using the Mirai botnet attack vector
- Dyn also was hit a month later in October 2016 with a peak of 1.5 Tbps
- Github was hit in February 2018 that only lasted 20 minutes but had a peak of 1.35 Tbps
One disturbing trend is that researchers found that there has been a huge rise in DDOS attacks from actual children. A new report from the UK’s National Crime Agency has found the average age for DDOS hackers has dropped to 15, with some miscreants as young as nine years old!
The Internet of Things (IoT) has also become weaponized for DDoS botnet attacks on network security. The number of internet-connected devices has increased as more connected home automation devices are developed and purchased by consumers, and many of these devices have poor security and password hygiene.
Ransomware is now being combined with DDoS attacks, as noted by Cloudflare, with a fifth of every DDoS victims also receiving a ransom attack seen in the several months during 2021 and 2022.
Different Types of DDoS Attacks
All DDoS attacks fall into two broad categories: those that are focused on your network security infrastructure itself, and those that are focused on applications, and in particular web-based applications.
There are two general types of attacks, ones that flood your infrastructure with garbage traffic to clog up your servers (called volumetric-based DDoS attacks) and ones that target specific protocols (called amplification attacks) such as Domain Name Services (DNS), Network Time Protocol (NTP), and other UDP-based services. The small protocol requests are amplified with much larger volumes of traffic generated by the server as a response.
Within these categories are several different attack types:
- SSL decryption-based exhaustion attack. These send garbage traffic to an SSL encrypted web server and tie it up in its response.
- SYN floods. This was one of the first kinds of DDoS botnet attacks and combines a volumetric traffic flood with an attack on the SYN protocol. By sending fake SYN requests, you can create a distributed botnet attack which can overwhelm a web server’s operations.
- NXNS attacks. This is a newer variation on the reflection attack by using a third-party to amplify a DNS request. It was discovered a few years ago by several Israeli security researchers.
- Simple Service Delivery Protocol attacks. This protocol is used by universal plug-and-play devices to discover new network resources. These attacks spoof a victim’s IP address and can create a botnet attack to send large traffic volumes that are reflected off these devices to a target web server.
How to Provide DDoS Protection?
The best way to provide DDoS protection for your network and to blunt DDoS attacks is to cover the complete waterfront of entry points to your network. This means understanding the entire potential attack surface area and being able to distinguish between normal and abnormal traffic patterns quickly and decisively. This also means being able to plan your defenses and so that you can scale up your protection when an attack increases the volume of the attack. Finally, you should use a web application firewall to block the most well-known attacks.
Sadly, there is no single product that will offer DDoS protection from every potential source and provide web security, cloud security and network security. But the good news is that over the years a number of specialized tools have been developed to help you protect your enterprise network against DDoS attacks.
Your burden is to ensure that there are no gaps in between these various tools, and that you have covered all the important bases to keep your network and applications secure and protect yourself against potential harm from cyber criminals. New security threats happen daily as attackers target your business, make use of inexpensive services designed to uncover weaknesses across your network or in the many cloud services that you use to run your business.
How A10 Can Help Prevent Botnet Attacks and Provide DDoS Protection
One way to provide DDoS protection is to deploy A10 Thunder® TPS product. It contains actionable automated detection intelligence and mitigation, with a three-second response time, powered by advanced machine learning and service discovery across hundreds of thousands of detection policies. Expert systems calculate blocking filters for your network traffic in real-time and the product comes in several different configurations, including hardware and virtual appliances.
You can find more specifics here. Thunder TPS can be integrated into any sized network and easily works with a variety of third-party protection solutions leveraging numerous open APIs. It can provide DDoS protection on attacks ranging from one to 380 Gbps.
Related Resources
- Comprehensive and Intelligent Network Security with A10 Networks (Solution Brief)
- Dodging and Defeating DDoS Attacks: Data Center Provider Guide (eBook)
- Global Gaming Company ZAPS DDoS Attacks in Real-Time with ZAPR (Case Study)
- What is the Mirai Botnet, How to Prevent DDoS Attacks? (Video)
- How to Analyze the Business Impact of DDoS Attacks (White Paper)