What is an Advanced Persistent Threat (APT)?
An advanced persistent threat is a threat actor or group of hackers of great ability and resources that can breach and exfiltrate data from a network. Tactics like social engineering, malware, ransomware, exploiting vulnerabilities, and zero-days are performed to achieve their malicious goals.
Though many cyber criminals operate independently, the Cybersecurity and Infrastructure Security Agency (CISA) and other agencies have linked cyber assaults to advanced persistent threat collectives, which are connected to certain nations who use them to further their agenda.
What does an Advanced Persistent Threat (APT) group do?
Advanced persistent threat actors, including those created by a nation-state, aim to enter a system without being noticed, stay there and sometimes build a back door or take data instead of damaging anything. They use malware to reach their goal, which may also involve accessing and exfiltrating data.
What are the Stages of an Advanced Persistent Threat Attack?
Advanced persistent threats consist of five stages and develop over time to evade discovery:
- Investigation: At the start, hackers gather data from multiple sources to identify their objectives. They have become more adept and might employ info from company websites and social media to target specific people in the business.
- Infiltration: Once inside a victim’s network, hackers spread malicious software to insecure systems and people. An advanced persistent threat starts with multiple cyber attack approaches such as social manipulation, spear phishing, taking login credentials, or a drive-by download.
- Discovery: In the discovery phase, hackers stay quiet and work slowly to prevent being found. They assess the organization’s cybersecurity protections, create a strategy, and activate many attack paths, including one for remote access.
- Occupation: Hackers break into unsecured systems over a long period without the victim being aware. The advanced persistent threat then secretly installs malicious software to steal sensitive business info such as emails, documents, designs, IP, or code.
- Exfiltration: Once the threat actors have obtained data, they wait for a chance to transmit it to the attacker’s control center for assessment and possibly more abuse and deception. The data may be sent through hacked servers or encrypted to make it harder to determine what was taken and where it is going.
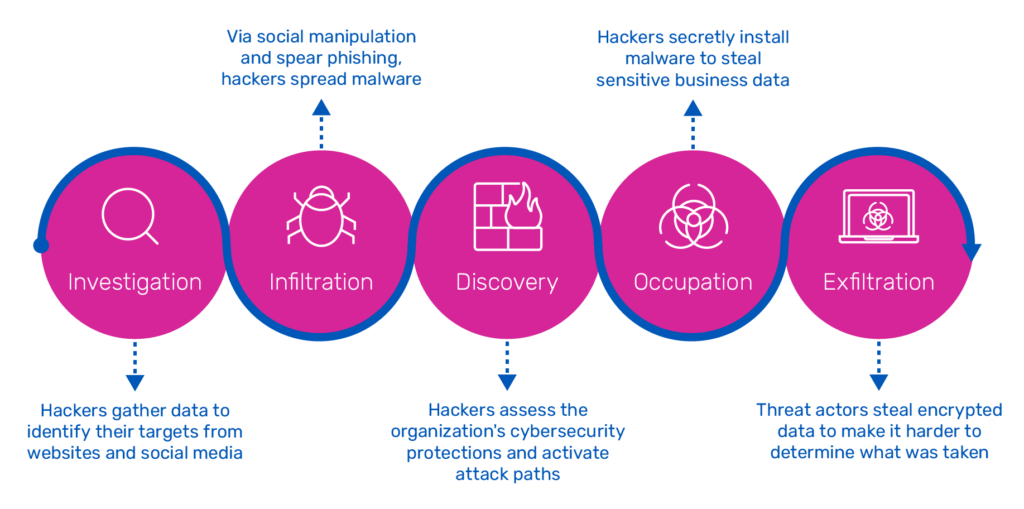
Five stages of an advanced persistent threat cyber attacks
How Big is the Advanced Persistent Threat (APT) Market?
Detection and removal of advanced persistent threats are problematic as they do not appear as malware and may be embedded deep in systems. So, they are hard to stop, which explains how the global Advanced Persistent Threat Protection Market is projected to expand to $15.1 billion by 2026, with a CAGR of 19.9 percent.
The creators of the advanced persistent threat are constantly adjusting the code to evade detection and shape the threat’s behavior. Without log or security information and event management (SIEM) tool analysis or outbound communication monitoring, a victimized organization may not realize they’ve been infiltrated until much later.
The need for malware protection systems like SSL/TLS inspection is rising due to a quickly changing threat landscape. These systems are already being used with significant effect in defense, government, finance, insurance, healthcare, and banking industries, causing the threat protection marketplace to expand.
The forensic analysis marketplace is expected to experience the most significant growth. The driving forces for the increasing demand for advanced persistent threat protection are technological advancements, cloud adoption by businesses, government regulations, and heightened awareness about protecting sensitive data.
What are Examples of Advanced Persistent Threat Actors?
1. Conti Ransomware (Russia)
Ransomware-as-a-service (RaaS) group, Conti, has gained infamy for its forceful methods and vast assaults on entities in the public and private sectors. With other notorious malware gangs, Conti has emphasized the need for a well-planned reaction to safeguard against potentially catastrophic losses of property, staff, and standing.
Russia-based Conti ransomware emerged in February 2020 and quickly became one of the most active ransomware groups. In August 2020, they established a data leaks site and leaked the data of over 150 companies by the end of the year, making them the third most active leaker group, behind Maze and Egregor.
Conti ransomware has become a staple cyber threat actor group. However, in August 2021, a former Conti associate revealed Conti’s ransomware tactics and framework and accused it of utilizing its partners for low-cost labor with minimal compensation. And then, in 2022, leaked private conversations between members caused speculation regarding its future.
2. Kimsuky (North Korea)
Kimsuky (a.k.a. Velvet Chollima, Thallium, TA406), a North Korean-backed cybercrime gang, has been active since 2017 but has existed since 2012. The group of hackers carries out espionage operations against South Korean think tanks, nuclear energy firms, and the Ministry of Unification, part of the South Korean government and works to reunite Korea.
The advanced persistent threat group has utilized stolen web hosting credentials from other victims to host their malicious scripts and tools. These credentials were likely obtained through spearphishing and credential harvesting scripts. Fake sites and services resembling Google or Yahoo mail were created on the victim domains, but the most common approach is to send an email with a malicious attachment.
3. Charming Kitten, APT35 (Iran)
Charming Kitten (also known as Phosphorus) has been a prominent Iranian cyberespionage group since 2014 when it orchestrated a complex internet spying operation via social media.
Since then, these threat actors have been behind numerous cyber attacks globally. In 2019, it targeted universities in the U.S., France, and the Middle East. In late 2020, it hit medical research organizations in Israel and the U.S. As of 2021, it is exploiting Microsoft Exchange Server vulnerabilities via ProxyShell.
By 2022, Charming Kitten had adapted new tactics to strike multiple targets. Intelligence was gathered with a new strain of malware, and they started using the tool, Hyperscrape, to surreptitiously steals emails from mailboxes.
4. Wicked Panda, APT41 (China)
By 2020, Wicked Panda (a.k.a Winnti, Barium, or Wicked Panda) had been established as a “workhorse” of cyber operations that help the Chinese government, according to cyber specialists and authorities from various agencies. The U.S. Secret Service stated that Wicked Panda is a “Chinese state-sponsored, cyber threat group” that is very good at carrying out espionage and financial crimes for personal and governmental benefit.
Experts describe the Chinese hacking model as a system of semi-autonomous espionage groups under the state’s control, with the Chinese government orchestrating cyber attacks.
Demian Ahn, a former assistant U.S. attorney who charged five Wicked Panda threat actors in 2019 and 2020, said evidence showed its vast reach and power. The defendants allegedly infiltrated governments and firms globally while executing ransomware attacks and cryptocurrency mining. They mentioned having thousands of machines simultaneously to acquire info and make illegal money. None of the five Chinese defendants have been extradited, and the cases remain unresolved.
5. OceanLotus Group, APT32 (Vietnam)
Cyber espionage unit, OceanLotus Group, breaches private sector companies in numerous industries, foreign governments, dissidents, and reporters. It employs powerful malware software and commercially available tools to execute operations that suit Vietnam’s state objectives.
In 2020, Bloomberg stated OceanLotus aimed to access data concerning the COVID-19 pandemic from China’s Ministry of Emergency Management and Wuhan’s authorities. The Vietnamese Ministry of Foreign Affairs dismissed the claims as baseless.
Kaspersky uncovered OceanLotus distributing malware via Google Play in 2020, and later that year, Volexity discovered the group had created bogus news sites/Facebook pages for profiling and malware dissemination. Facebook tracked it to CyberOne Group in Ho Chi Minh City, Vietnam.
How do you Prevent Advanced Persistent Threats?
In the past, organizations tried to protect their security via additional products to the cybersecurity stack. With so many vendors and products, it takes much work to manage, and it is expensive. To counter this, the best approach is one platform combining various technologies and solutions to fight against advanced persistent threats.
To protect against cyber attacks,
- Rapidly detect and stop unknown malware, exploits, and threats
- Recognize infected users and examine potential intrusions associated with threats at the internet edge, in mobile devices, and in the data center
- Prevent malicious actors from moving laterally
But how? A10 Thunder® SSL Insight® is a TLS/SSL decryption system that decrypts all port traffic, allowing third-party security appliances to inspect all organization traffic without sacrificing performance.
Thunder SSLi eliminates the encrypted blind spot by taking the heavy lifting of decrypting and encrypting off third-party security devices while still adhering to privacy standards.
Security devices offer a thorough traffic inspection but cannot encrypt or decrypt quickly. Additionally, some cannot decrypt at all. Thunder SSLi boosts existing security measures, protecting investments in security infrastructure and enhancing a Zero Trust model strategy.
Related Resources
- Mitigating DDoS Attacks and Malware Spread (Webinar)
- Decrypting SSL to Uncover Hidden Threats (Webinar)
- Combating the Surge of Modern Malware and Ransomware (eBook)
- Centralized TLS Decryption: The Prerequisite to SASE, SSE, Zero Trust (Blog Post)
- This Month in Ransomware: Hospitals and Patients Affected (Blog Post)
