What are SSL/TLS Decryption and SSL/TLS Encryption?
- Stored on cloud-based repositories or devices on your network
- Retrieved and transmitted through email, collaboration tools, and other business systems
- Processed through Software as a Service (SaaS), Infrastructure as a Service (IaaS), and Platform as a Service (PaaS) systems
Protecting Your Vulnerable Data
The security of all this data is vital to a company’s operations. What’s more, some data protections against cyber criminals are now mandated by various laws and regulations in the United States and globally. So, it’s incumbent upon organizations to maintain visibility into their network traffic, protect their data, and ensure legal compliance. That all starts with the adoption of a Zero Trust model—one that authenticates all traffic coming into a network to prevent access by cyber criminals. A10 Thunder® SSL Insight (SSLi®) is one product that is built specifically to help you conquer this challenge.
Pivotal to a Zero Trust architecture are SSL/TLS encryption and SSL/TLS decryption. SSL, which stands for Secure Sockets Layer, and TLS, which stands for Transport Layer Security, are both security protocols used in the encryption and decryption of data. SSL security was developed first: SSL encryption/SSL decryption was created in 1995, then evolved into the more sophisticated TLS encryption/TLS decryption in 1999; however, SSL security and TLS security work similarly and are lumped together by name. It’s worthwhile to learn more about SSL encryption/SSL decryption and why it grew to become TLS encryption/TLS decryption.
The Growing Threat Landscape
What do Yahoo, Alibaba, LinkedIn, Facebook, and Marriott all have in common? They are among the companies with the dubious distinction of experiencing the biggest data breaches of the 21st century, according to a July 2021 article in CSO. Since then, data breaches have only become a bigger threat. Infosecurity Magazine revealed that 108.9 million accounts were breached in the third quarter of 2022, which represents a 70 percent increase over the second quarter.
The growing threats to network security by cyber criminals make it ever more vital that companies use SSL encryption/TLS encryption and SSL decryption/TLS decryption as they create their Zero Trust architecture and tech stack. For more information about the importance of these protocols, see our article “TLS/SSL Decryption Essential for Strong Zero Trust Strategy.”
The Legal and Monetary Implications
Unlike the European Union, which enacted the comprehensive General Data Protection Regulation (GDPR), the United States doesn’t yet have an all-encompassing data privacy law. Rather, protections are mandated by various state laws, plus a federal law protecting minor children’s online information, the Children’s Online Privacy Protection Act, a federal law protecting your credit card data, Payment Card Industry security standard, or PCI, and a federal law protecting health information, Health Insurance Portability and Accountability Act, or HIPAA.
But U.S. state data protection laws are continually expanding. The not-for-profit group International Association of Privacy Professionals (IAPP) lists these new state privacy protection laws that take effect in 2023:
- California Privacy Rights Act of 2020 (CPRA)
- Colorado Privacy Act (CPA)
- Connecticut Data Privacy Act (CDPA)
- Utah Consumer Privacy Act (UCPA)
There can be steep monetary penalties for failing to protect data from cyber criminals. In the United States, the largest fine for a data breach was imposed on Equifax in 2017 by the Federal Trade Commission to the tune of US$575 million. Meanwhile, in the European Union, with its tough laws around data privacy and steep fines for data breaches, Amazon was fined a whopping US$877 million in 2021 for cookie violations prohibited by the EU’s GDPR.
Beyond fines and penalties, companies do incur additional costs as a result of data breaches. These costs come about through lost revenue, additional human resources and software expenditures to repair the damage, and marketing and PR efforts to mitigate the hit to a company’s reputation and trustworthiness.
How SSL/TLS Encryption and SSL/TLS Decryption Work
As you saw above, your data, which could include files, communications, or other assets, is at risk whether it’s in transit or stored in a networked device or cloud-based repository. To guard against these threats and implement a Zero Trust security model, your company needs to encrypt your data. Encryption is the disarranging of your data so that’s indecipherable in case it falls into the unauthorized hands of cyber criminals.
Encryption is based on complex mathematical algorithms, also called ciphers. Currently, the most trusted encryption algorithm is the Advanced Encryption Standard (AES); it’s used by the United States government and numerous companies and organizations. Encryption algorithms scramble your data to make it unintelligible to unauthorized cyber criminals who may hack into your information repositories or intercept your information while it’s in transit.
SSL security requires data to be encrypted by the sender using an encryption key. As the recipient, you need a decryption key provided by the data owner or sender in order to be able to decrypt the data and make sense of it. Much like your own personal passwords, cryptographic keys are stronger the longer and more complex they are.
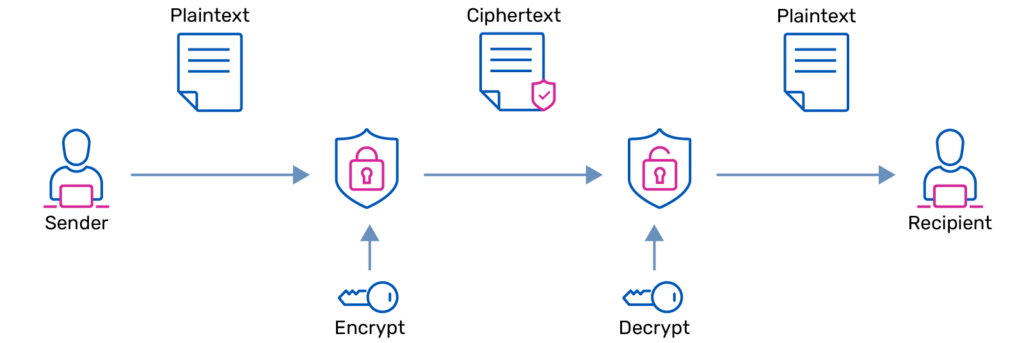
Messages are decrypted and encrypted using different keys
Tools for Effective SSL/TLS Encryption and SSL/TLS Decryption
Consider A10 Thunder SSLi, a powerful solution that helps companies implement a foundation on SSL security, that is SSL encryption/TLS encryption and SSL decryption/TLS decryption. This product fully supports your Zero Trust architecture: It decrypts incoming network traffic; inspects it for malware, viruses, and phishing; isolates any security threats; then re-encrypts the authorized traffic and allows it to proceed. Read more about how A10 Networks supports Secure Sockets Layer (SSL).
Implementing an SSL security-based approach with SSL encryption/TLS encryption, managing cryptographic keys, and analyzing the traffic entering or attempting to enter your network are all essential requirements for the Zero Trust security model. But at the same time, this heavy computing workload puts pressure on your security infrastructure, resulting in performance degradation. It seems like a catch-22.
In this situation, SSL offloading can come to your rescue. With SSL offloading, the computing-intensive work of encrypting and decrypting SSL/TLS-based traffic gets moved to a separate server dedicated just to encryption and decryption. Being relieved of this computing burden, your security infrastructure can be freed up to perform better.
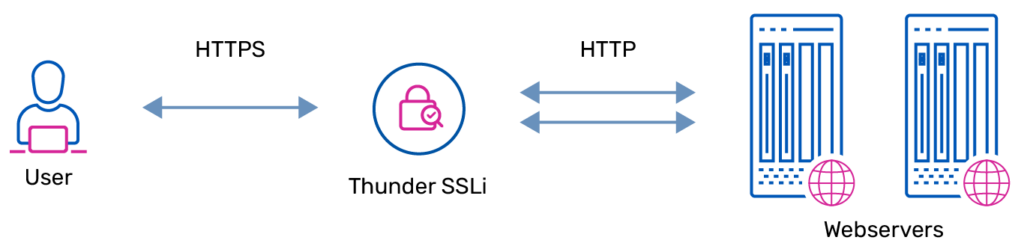
SSL Offloading example with Thunder SSLi in the middle doing the heavy lifting
To reap the benefits of SSL offloading, companies need to invest in an application delivery controller (ADC), which is the network appliance that actually performs the decryption and re-encryption of data entering the network. Be sure to learn about the A10 Thunder Application Delivery Controller. The evaluation and use of an ADC is a whole topic in itself; get more details in our article “Evaluating a TLS/SSL Decryption Solution.”
To get more information and context for network security basics, plus a deep and wide dive into the challenges companies currently face and productive ways to move forward, read our free eBook, “The Ultimate Guide to TLS/SSL Decryption.”
Related Resources
- Zero Trust, Cloud and Remote Working Drive Digital Resiliency (Blog)
- Zero Trust Architecture: 5 Reasons You Need It (Blog)
- The Ultimate Guide to TLS/SSL Decryption (eBook)
- A Closer Look at Zero Trust Cybersecurity Strategy Adoption (Blog)
- Zero Trust is Incomplete Without TLS Decryption (White Paper)
- Ransomware, Phishing, Zero Trust, and the New Normal of Cyber Security (Blog)
- Evaluating a TLS / SSL Decryption Solution (Blog)
- Defeat Cryptojacking with Decryption and Inspection (Blog)
- TLS/SSL Decryption Essential for Strong Zero Trust Strategy (Blog)
- SSL Decryption: Security Best Practices and Compliance (Blog)
