What is the Log4j vulnerability, Log4J CVE?
An Unprecedented Zero-day Vulnerability Invites Threats from Malware to Botnets and DDoS Attacks
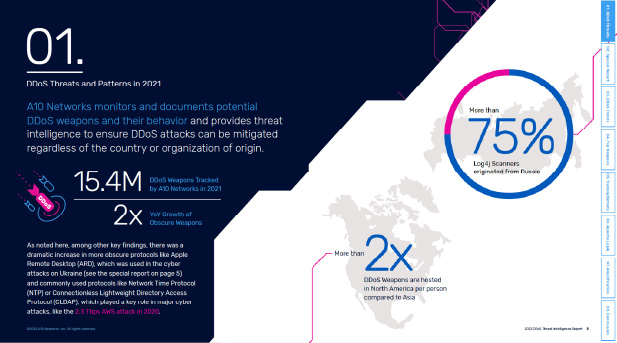
It’s no exaggeration to call the Log4j vulnerability one of the most severe cybersecurity crises in many years. A flaw in the widely popular open source Log4j software package, the Log4j CVE exposed a vast number of organizations worldwide to malware, including the mass recruitment of botnets for DDoS attacks. As a zero-day vulnerability, the Log4j CVE may already have been exploited by cyber criminals before it was first reported to the Apache Software Foundation on November 24, 2021, or announced publicly on December 10, 2021.
The unprecedented extent of the zero-day Log4j vulnerability has made remediation both critical and challenging. The Log4j CVE affects hundreds of millions of devices from network servers and heavy industrial equipment to automobiles, printers, and smartphones, and popular services such as Cloudflare, iCloud, Minecraft: Java Edition, Steam, Tencent QQ, and Twitter—all of which must be updated to a new version of the software to avert a Log4j exploit.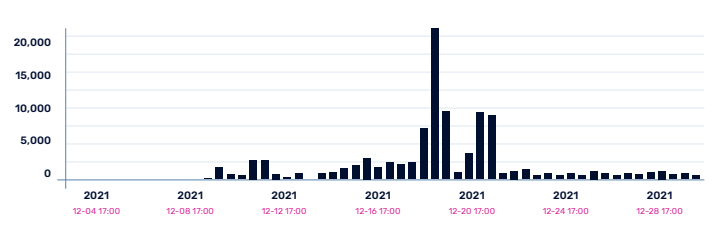 As early as December 9, 2021, the A10 security research team began scanning for hosts that were affected by the Log4j CVE.
As early as December 9, 2021, the A10 security research team began scanning for hosts that were affected by the Log4j CVE.
How the Log4j CVE Works
First released in early 2001, Log4j is a subsystem for recording events such as error and status reports. Lightweight and easy to use, Log4j quickly became a common component of modern applications. However, the use of the Java Naming and Directory Interface (JNDI) in the package left it open to exploitation by criminals.
By sending fraudulent HTTP/HTTPS requests to log an event, and including a JNDI request in its header, an attacker might trick Log4j into querying the hacker’s own LDAP server, which could then respond with directory data containing a malicious Java object. In this way, the Log4J exploit allows cyber criminals to launch remote code execution (RCE) attacks to obtain full access to the target computer.
Cyber Criminals Capitalize with Botnets, DDoS Attacks, Malware, and More
The disclosure of the zero-day Log4j CVE sparked a dramatic response by cyber criminals, from Log4j exploit testing to active attacks. Within days, an Iranian state-sponsored hacking group named Charming Kitten or APT35 launched multiple Log4j exploit attacks against Israeli government and business sites. New Log4j exploit mutations and variations proliferated quickly, and by the end of 2021, the advanced persistent threat (APT) Aquatic Panda was using Log4Shell exploit tools in an attempt to steal industrial intelligence and military secrets from universities. Meanwhile, botnets such as Mirai, Elknot, and Gafgyt were leveraging the Log4j vulnerability to compromise IoT devices including IP cameras, smart TVs, network switches, and routers.
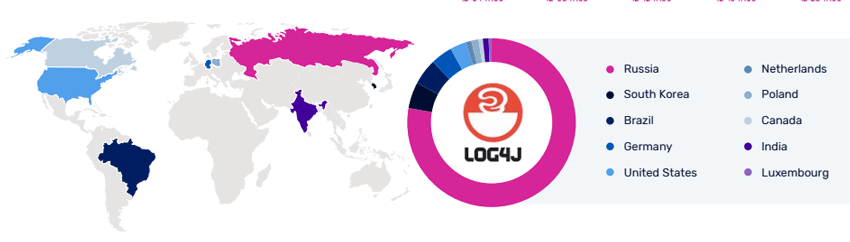
Log4j Exploit Distribution by Country
Given the widespread presence of Log4j in IoT devices, the use of the Log4j CVE to recruit botnets is particularly problematic. With patching efforts likely to drag on—or be neglected entirely—for months or years, cyber criminals will have ample opportunities to recruit vulnerable devices for crypto mining and DDoS attack platforms. Mirai, in particular, remains a perennial threat against victims of all sizes, both directly and when rented to other threat actors to launch attacks of their own.
Other forms of malware have exploited the Log4j vulnerability, as well. Even before the end of 2021, the Belgian Defense Ministry discovered such an attack against its network, possibly as part of a ransomware scheme. In early January 2022, Microsoft confirmed that cyber criminals were targeting VMware Horizon server software at organizations including the UK National Health Service (NHS) to install NightSky, a newly developed ransomware strain based on the Log4j exploit.
B1txor20, first identified in March 2022 by researchers at Qihoo 360’s Network Security Research Lab, deploys backdoors, SOCKS5 proxy, malware downloading, data theft, arbitrary command execution, and rootkit installing functionality. Using the Log4j exploit, the malware attacks Linux ARM, X64 CPU architecture and uses DNS tunneling to receive instructions and exfiltrate data to and from the botnet’s command and control servers.
Protecting Your Organization Against Log4j Exploits and Other Zero-day Threats
The Apache Foundation responded quickly to the disclosure of the Log4j CVE by releasing a series of updated versions, and finally publishing a completely secure release, version 2.17.1, on December 17, 2021. However, as cybersecurity professionals know all too well, the availability of a security patch does not equate to actual security. As noted by the Google Security blog soon after the vulnerability was announced, more than 35,000 Java packages were likely affected, with most affected five levels down or more. “These packages will require fixes throughout all parts of the tree, starting from the deepest dependencies first,” the company cautioned.
While upgrading or disabling Log4j libraries throughout the organization—including IoT devices and employee-owned laptops and smartphones—is a daunting task, it is an absolutely essential requirement. Beyond this critical task, enterprise cybersecurity teams should also take steps to minimize the risk of a Log4j exploit. A web application firewall should be deployed and configured to filter out unauthorized sources and content, including the JNDI requests used in Log4j RCE attacks, from unknown IP addresses. Similarly, JNDI lookups can be disabled to prevent queries to a malicious LDAP server. Disabling the loading of remote Java objects can also help ensure that malicious code will not be installed into the environment.
Preventing IoT and other devices from being recruited into botnets, often for use in DDoS attacks, has been a key cybersecurity priority since long before the emergence of the Log4j exploit. The Log4j vulnerability greatly increases this risk, especially given the spike in DDoS activity associated with the Ukraine-Russia conflict. Often, these attacks use methods such as DDoS amplification and reflection to multiply their impact via open NTP, LDAP, and SNMP services.
In response, organizations must redouble their defenses against both botnet recruitment and DDoS attacks. This begins with securing the enterprise network, reducing the attack surface, and maintaining an inventory of internet-exposed IoT assets. Reducing the number of open NTP, LDAP, and SNMP services can thwart DDoS amplification and reflection tactics. Sluggish network performance can signal an active botnet infection and should trigger a rapid response by SecOps teams.
How A10 Networks Protects Your Organization Against Log4j Exploits and Other Zero-day Threats
A10 Networks offers advanced cyber security solutions to support a Zero Trust strategy to help businesses protect their networks and data. These solutions include:
- The Thunder® Threat Protection System (TPS) employs advanced DDoS protection and mitigation strategies to protect against DDoS attacks.
- The Thunder SSL Insight® (SSLi®) provides full network traffic visibility making it hard for attackers to sneak malware into networks or exfiltrate data.
- The Thunder® Convergent Firewall (CFW) is a scalable high-performing firewall that supports IPsec VPN, secure web gateway, DNS over HTTPS (DoH), and CGNAT with integrated DDoS protection.
- The A10 Harmony® Controller, supports centralized management for A10 Networks’ Thunder portfolio including ADC, SSLi, CFW and CGN products.
A10’s modern DDoS protection solution, Zero-day Automated Protection (ZAP), scrubs attack traffic quickly and effectively using multi-level adaptive mitigation policies and ML-powered ZAPR (zero-day attack pattern recognition).
Related Assets
- Time for Zero-day DDoS defense (Blog Post)
- How Zero Trust Could Have Stopped DarkSide’s Ransomware Malware (Blog Post)
- Speed Response with Automated Zero-day DDoS Defense (White Paper)
- Global Gaming Company ZAPS DDoS Attacks in Real-Time with ZAPR (Case Study)