Understanding DDoS Attacks
It’s clear the DDoS attacks aren’t going anywhere — in Q2 2017, the number of attacks increased significantly compared with the same quarters in 2015 and 2016, according to a report Q2 2017 DDoS Attack Trends Report from CDNetworks.
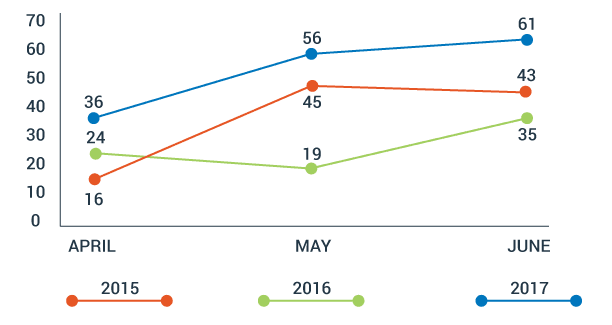
Number of DDoS Response Times by Month in the Q2 of Each Year
Consequently, it’s more crucial than ever for companies to have a deep understanding of how DDoS attacks work and how they can improve their defenses against them.
The Anatomy of DDoS Attacks: Volumetric, Network, Application webinar from Randy Smith of Ultimate Windows Security and Don Shin of A10 Networks explored those topics in-depth. Here, we’ll dig into the webinar and explain the different types of DDoS attacks, mitigation tips and mitigation solutions that work.
What You Need to Know About DDoS Attacks
Before we take a deeper dive into the details of DDoS attacks, let’s first review the basics.
In the past, DDoS attacks were usually carried out by attackers who were motivated by politics, hacktivism or simply a nihilistic outlook.
Today, however, DDoS attacks can also be used as a means of extorting money from companies. Since large companies tend to have active ties with law enforcement, specialized security teams and greater computing capacity, small and medium businesses are a particularly attractive target for extortion-based DDoS attacks (although large companies certainly aren’t immune).
Money isn’t the only motivator, however—disgruntled employees have been known to launch DDoS attacks as a form of revenge. For example, in May 2018, a New Mexico man was sentenced to 15 years in prison for using DDoS attacks to target a number of companies, including those he used to work for.
Alternatively, attackers may use DDoS attacks as a smoke screen to mask other nefarious activities, such as data exfiltration.
Worse, as DDoS services become more and more affordable, an increasing range of people have the ability to cripple company networks in a matter of seconds.
In the end, companies are the ones who shoulder the largest expenses—while an individual might pay under $1,000 to launch a DDoS attack, the average cost of a DDoS attack is $123,000 for small businesses and $2.3 million for enterprises.
Four Types of DDoS Attacks
Currently, there are four types of DDoS attacks:
- Volumetric
- Network transport
- Application
- Multi-vector
Volumetric attacks are what most people think of when they hear about a DDoS attack: A veritable deluge of packets.
However, the two other types of DDoS attacks can be just as disastrous. Network transport attacks take place within the network protocol layer, while application attacks take place within the application itself.
Let’s dig deeper into each type of attack.
Volumetric
The goal of volumetric DDoS attacks is to consume all available network bandwidth between the victim and the internet by overwhelming the target with a flood of data. In this way, attackers prevent legitimate users from accessing the network.
So, how do attackers send that much data, and how do they prevent it from being filtered out at the gateway? With the help of three tools:
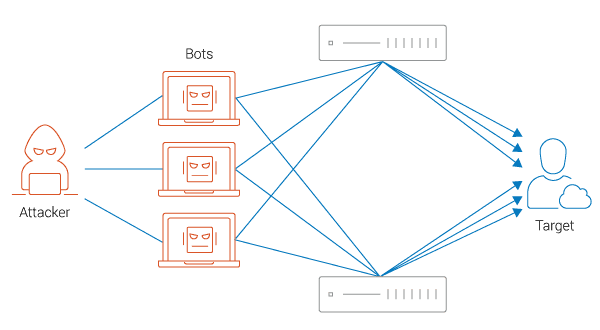
- Botnets: A network of hijacked internet-connected devices (such as servers, private computers and mobile devices) that are used to send massive amounts of data to the target.

Botnets DDoS Attack
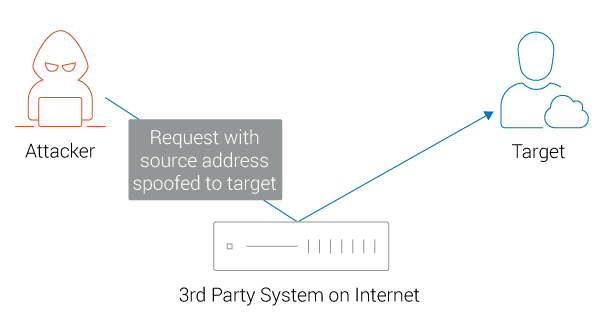
- Reflection: An indirect method of sending traffic that prevents the target from seeing the IP address behind the flood of data.

Reflection DDoS Attack
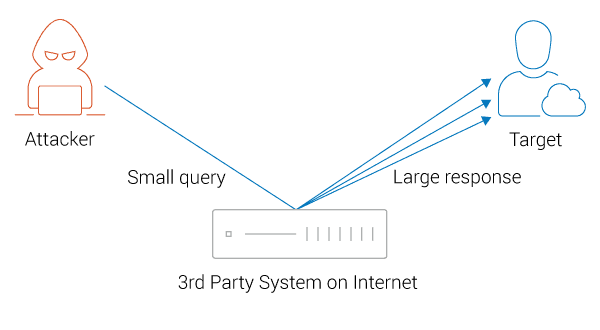
- Amplification: A technique that allows attackers to consume a relatively small amount of bandwidth while simultaneously increasing the amount of data being sent to the target.

Amplification DDoS Attack
When you put all three elements together, you get a massive volumetric attack that effectively dominates the target’s bandwidth.
Network Protocol
Given the rapidly growing prevalence and numerous security vulnerabilities of the Internet of Things (IoT), it doesn’t come as a shock that hackers have used those vulnerabilities to their advantage.
The goal of a network protocol-based DDoS attack is to render the target inaccessible by exploiting a protocol weakness, typically in layer three or four.
This is accomplished using a variety of techniques:
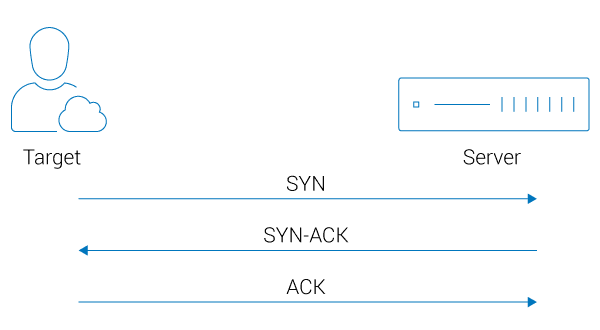
- SYN flood: SYN floods are specific to the Transmission Control Protocol (TCP). In short, TCP protocols allow applications enable data transfers using a process known as a three-way handshake. Before a data transfer can take place, a SYN command needs to be sent by the client, which is then answered by a SYN acknowledgement (SYN-ACK) from the server, which in turn is answered by a final acknowledgment (ACK) from the client.

SYN Flood DDoS Attack
Attackers can exploit this process by sending a large number of SYN commands to the server. This overwhelms the server’s capacity and results in a backlog queue and, if the SYN commands keep coming in, an overload. Often, hackers will use SYN floods to assess the capacity of the target’s servers before launching an even bigger attack.
- Ping attack: This method is similar to the SYN flood method, but in this case, a vast amount of simple Internet Control Method Protocol (ICMP) echo requests, also known as pings, are used to flood the target’s network.
- UDP flood: With UDP floods, attackers send a great number of packets, which contain User Datagram Protocol (UDP) datagrams, to random ports. Because the port will send a response back to every packet that it receives, it can quickly become overwhelmed.
Application
With this type of attack, hackers exhaust a resource at the application layer, either by attacking the web server itself, a web application platform or a web application.
The resources they aim to exhaust could lie within the operating system (such as the CPU, input/output or storage) or within an application (such as session state).
Essentially, application-based network protocol attacks use an application to send so many requests to a server that it reaches and exceeds its capacity. Since most application developers aren’t trained to counter targeted strikes, this type of attack can be particularly difficult to remedy.
HTTP floods are a popular way of carrying out application-based DDoS attacks. To use this method, hackers must first identify a GET or POST request (the two most common types of HTTP requests) that demands a great deal of work from the server. When enough of these requests are sent, the server gets bogged down by phony and labor-intensive requests.
HTTP flood
Multi-Vector
Unfortunately, as it’s become increasingly easy for hackers to launch DDoS attacks, it’s also become increasingly common for them to launch more than one type of attack at the same time.
That brings us to the fourth type of attack, known as the multi-vector attack. In this case, hackers use multiple types of attacks at once in order to discover where the target’s biggest vulnerabilities lie, or to increase their attack’s chances of success.
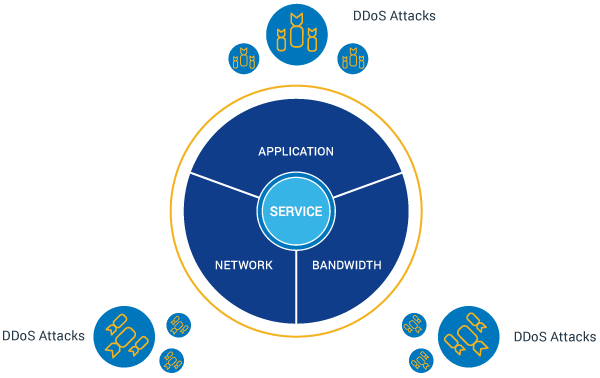
Multi-Vector DDoS Attack
For example, a hacker could simultaneously carry out both a volumetric and network protocol attack against a target. In this way, if one attack fails, the other attack may be able to succeed.
And, this is far from uncommon—in fact, multi-vector attacks account for 75 percent of the 3,000 DDoS attacks that occur daily. The Mirai botnet, which was used to attack a variety of targets in 2016, contained a whopping 10 different kinds of attack vectors.
This type of trend illustrates just how quickly DDoS attacks and their many variants are becoming very real possibilities for companies of all sizes.
In our next article, How to Defend Against DDoS Attacks: Six Steps, we discuss how companies can best defend against DDoS attacks and implement best practices.
Webinar
Watch our webinar “Anatomy of 3 DDoS Attacks: Volumetric, Network Application” to learn more about DDoS attacks, how they work and what you can do to prevent and mitigate them.
Learn more about A10’s DDoS Protection solutions.
Seeing is believing.
Schedule a live demo today.