The Global State of DDoS Weapons

In the past couple of years, the world has been battling the COVID-19 pandemic. As we slowly work our way back to normalcy in the real world, the cyber world still seems to be engulfed by a new pandemic of cyber attacks with each passing day.
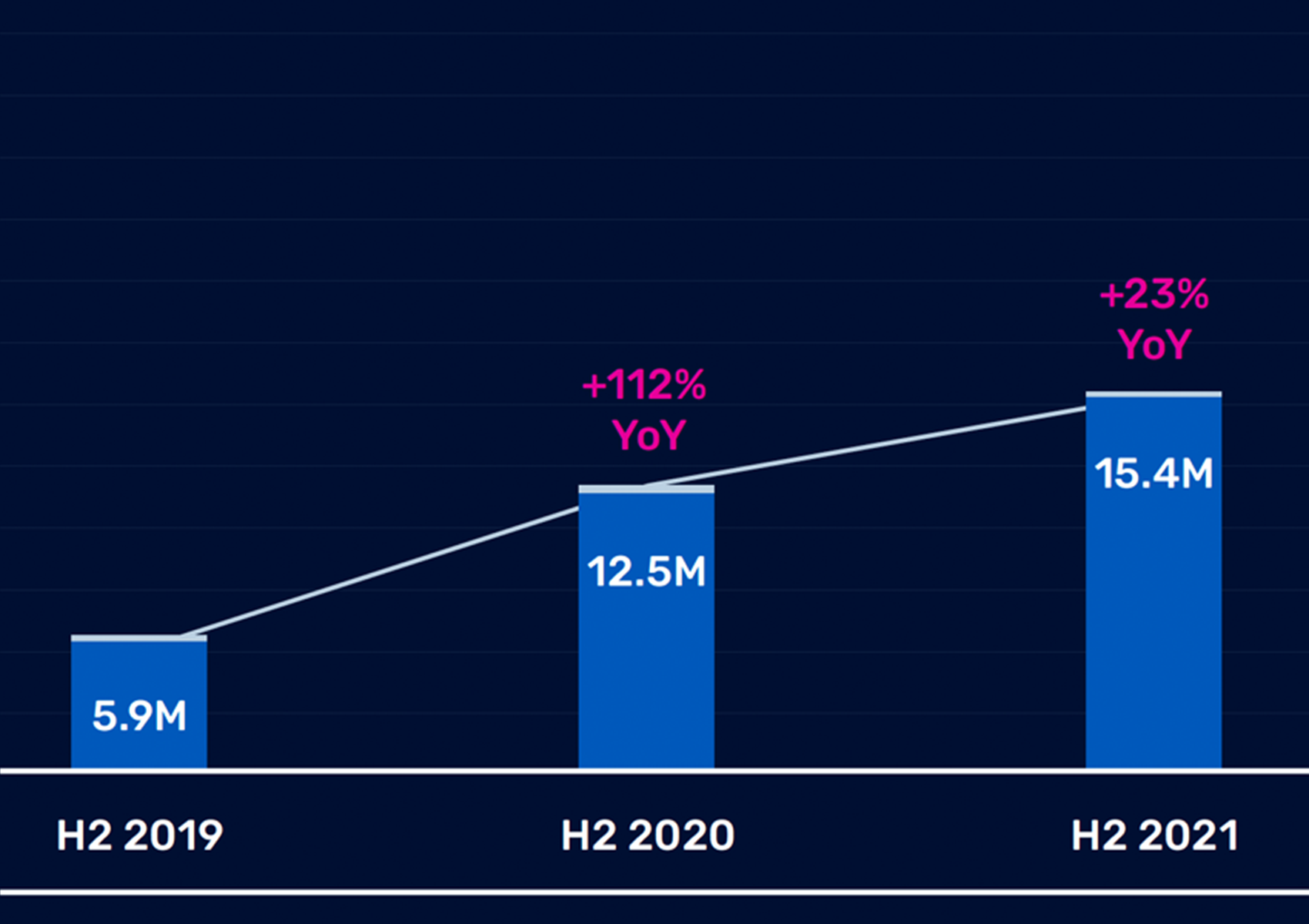
In the second half of 2021, we saw some interesting developments in the area of cybercrimes, including events like attackers leveraging the now notorious Log4j vulnerability, and Microsoft mitigating one of the largest DDoS attacks ever recorded. We also observed 23% YoY increase in the total number of DDoS weapons available. These could easily be exploited for use in DDoS attacks.
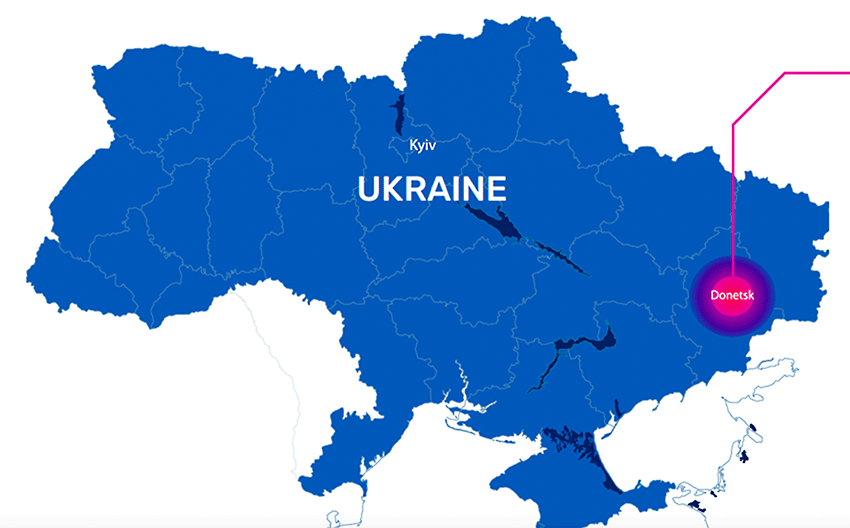
In addition, at the beginning of 2022, we saw the Ukraine-Russia conflict take a turn for the worse, turning into an all-out war. In conjunction with the ground war, we observed a number of cyberattacks targeting Ukraine government networks and infrastructure. The latest edition of the Global State of DDoS Weapons report contains a special highlight section detailing the use of DDoS attacks in the Ukraine-Russia conflict to disrupt critical infrastructure and communications.
The A10 security research team observed significant and sustained attacks on Ukrainian government networks and commercial internet assets, with a massive spike on the first day of the conflict. These cyber warfare tactics didn’t stop on the first day though and have continued.
In addition, the report includes a spotlight section featuring the Apache Log4j vulnerability, what that means for DDoS attacks, and how organizations can protect themselves against this vulnerability by incorporating principles of Zero Trust into their security strategies and by taking solid preventive measures.
The report also provides detailed insights into specific DDoS weapons and DDoS attack activities observed around the globe including the use of malware in the recruitment of botnets.
Key insights from the report:
- China hosts the highest number of DDoS weapons, including both amplification weapons and botnet agents
- 100% YoY growth of obscure weapons like Apple Remote Desktop (ARD)
- Twice as many DDoS weapons hosted in North America per person compared to Asia
- More than 75% Log4j scanners originated from Russia
To learn more about the current state of cybersecurity and how you can protect your organization against modern DDoS attacks as well as the role you can play in stopping malware and botnet propagation, download the full report.