Importance of Securing and Simplifying DNS Infrastructure

Domain Name System (DNS), informally referred to as the “phonebook of the internet,” is one of the mainstay protocols that makes the internet work by translating reader-friendly domain names into IP addresses and vice-versa.
While enabling user interaction with the internet is undoubtedly one of the most fundamental benefits of DNS, it is also critical to the normal functioning of numerous applications and services, including mobile apps, email, voice-over-IP (VoIP), etc. Similarly, many security constructs are based on DNS names, such as X.509 certificate for a website, which identifies a website by its DNS name.
Many enterprises and service providers provision their own DNS infrastructure. This is done to ensure proper and uninterrupted operations of their own infrastructure and business applications, as well as to provide it as a service to their end users. For example, in many organizations, work computers default to using the organization’s own DNS servers. This helps internal users access internal websites while keeping such domain names confidential and secure.
This deployment of DNS infrastructure, however, introduces its own set of security challenges. This is because DNS infrastructure is one of the favorite targets of attackers, primarily because of two reasons:
- DNS is an inherently insecure protocol, and hence, it is easier to target.
- DNS is fundamental to the operations of the internet and applications, and therefore bringing down the DNS can have a much greater impact as compared to targeting just individual applications or services, such as web servers.
For example, here is a typical flow of DNS resolution process:
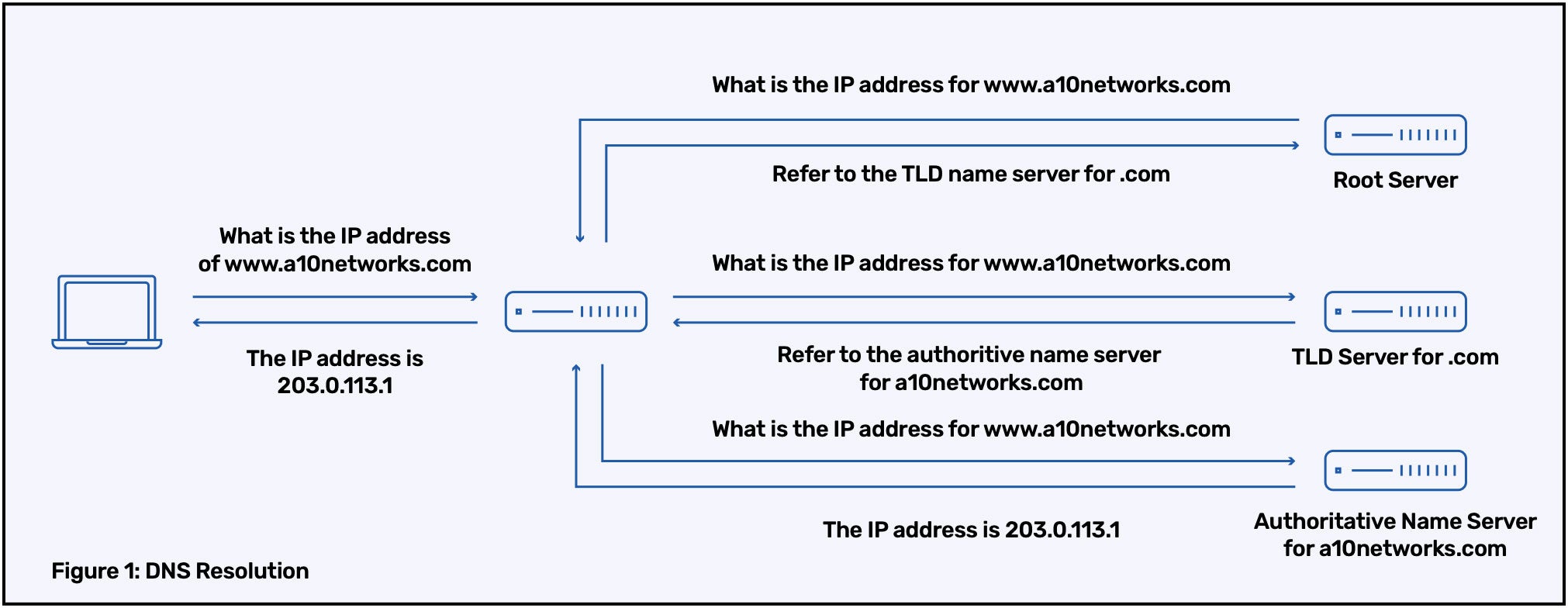
In this, all communication, both between the client and the local DNS resolver, and between the local DNS resolver and the name servers for the various zone levels, takes place in clear text. Moreover, there is no validation of the DNS response to ensure that it comes from an authentic source or that it has not been modified in transit.
Due to these vulnerabilities, over time, various types of DNS threats emerged. Some of the common and well-known threats include eavesdropping, DNS hijacking, NXDOMAIN flood attacks, and malware-infected hosts contacting C&C centers.
As these threats emerged and evolved, so did the technologies to combat these threats, including DNSSEC, DNS response rate-limiting, and more recently, DNS over HTTPS/TLS, among others.
Challenges with the traditional DNS infrastructure
With the emergence of each new threat and the technology to counter it, organizations have traditionally responded by deploying a new security product to remediate the immediate threat at hand. Over time, this has led to deployment of numerous security devices in the network, resulting in the following challenges:
Increased complexity: With many security devices in the network, the task of deploying, managing, and troubleshooting has become increasingly complex. Each device has its own separate management interface and configuration commands, and therefore, requires specialized knowledge to deploy and troubleshoot. This also increases the risk of misconfiguration that can lead to security gaps, or even DNS connectivity issues.
Increased cost: Many devices in the network means that upgrading DNS infrastructure to meet growing traffic needs will require upgrading most, if not all, such devices. This means one needs to evaluate and purchase multiple different products, resulting in high purchase and licensing costs.
Slow performance: Some of the newer DNS technologies, such as DNS over HTTPS (DoH) and DNS over TLS (DoT) require TLS decryption/encryption processing, which is highly CPU-intensive. However, DNS servers were not originally designed for such processing, and hence adding DoH/DoT can lead to a severe slowdown in the overall performance of existing DNS infrastructure.
Unsuitable for hybrid cloud: All these problems of complexity, costly upgrades and slow performance are further compounded by the growing adoption of hybrid cloud. This is because many of the legacy security products that have been deployed in private data centers may either not be available or may not be optimally suited for such a deployment. This leads to adoption of cloud-specific offerings, adding to the complexity and cost of deploying and maintaining DNS infrastructure.
How A10 Can Help
To deal with these challenges, one needs to reevaluate the existing DNS infrastructure and devise methods to secure and consolidate it. With A10’s high-performance DNS security solutions, DNS operators can do so in a cost-effective manner, while still meeting the performance requirements of newer technologies such as DoH/DoT.
To learn more, see the A10 white paper Challenges and Recommended Best Practices to Secure DNS Infrastructure. In this white paper you’ll learn about:
- The importance of securing a DNS infrastructure
- The common types of DNS attacks
- Limitations to traditional approaches to securing the DNS
- Solutions for countering DNS attacks