How to Identify and Block an Application Attacker

Attacks against applications have become increasingly common. In this post, we explain how you can identify and block an application attacker using A10 Lightning Application Delivery Service (ADS) and A10 Harmony Controller.
The Problem – Application Attacks
Attacks on web applications are becoming a major problem – it’s a trend that’s on an upward swing. Reports suggest that application layer attacks on web applications are will grow 17.34 percent from 2014 to 2019.
The OWASP publishes a list of common vulnerabilities found in web applications. Typically, poor coding practices lead to these vulnerabilities. When a library or operating system becomes vulnerable, every application using that library also becomes vulnerable.
Attackers use layer 7 (application layer) techniques like SQL-injection, Command-injections, Cross-site Scripting (XSS), Cross Site Request Forgery (CSRF) and more to attack a web application and attempt to extract sensitive data.
The Solution – WAF
In a perfect world, using coding best practices would prevent vulnerabilities in web applications. But in reality, working with many software pieces that may have vulnerabilities often makes it impractical to address all vulnerabilities before releasing the software or fixing it as soon as the vulnerabilities are discovered.
In such a scenario, a Web Application Firewall (WAF) becomes a must-have component in the application delivery infrastructure. WAF applies Deep Packet Inspection (DPI) techniques to scan every HTTP request and response to identify any malicious content. Most WAF products come with a feature that enables them to block the traffic containing malicious content. DPI, however, can be expensive and resource intensive because it must check every bit without a significant impact on the overall response time.
Elastic WAF
A typical WAF appliance deployed in front of application servers will quickly start choking when an attacker sends a lot of traffic to the server to exploit vulnerabilities. With A10 Lightning ADS, however, the Harmony Controller triggers the elasticity and increases the number of Lightning ADCs to handle more traffic. Therefore, overall traffic is not affected. However, scaling out creates additional infrastructure costs. And while scaling out and increased costs are acceptable for increases in legitimate traffic, it may not make sense for malicious traffic.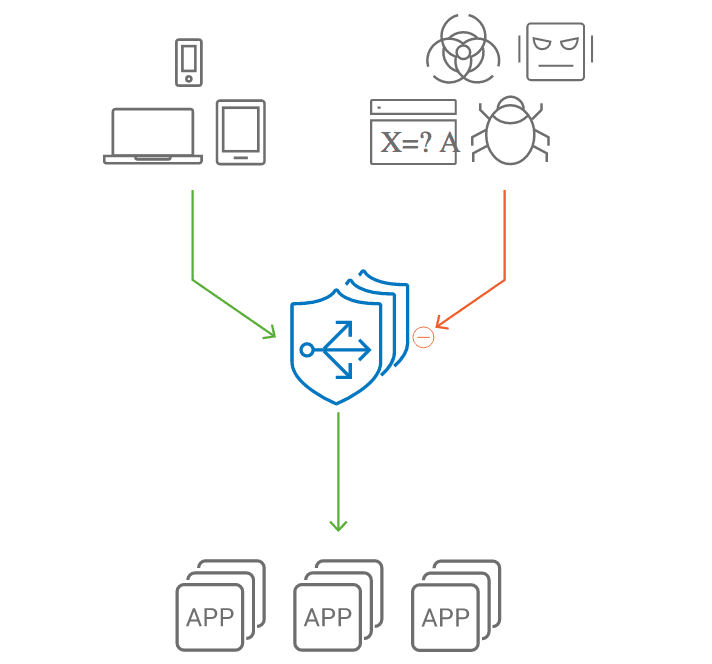
Reducing Costs with A10 Lightning ADS
A10 Lightning ADS is a cloud-native solution to optimize the delivery and security of applications and services running over public clouds or private clouds. Lightning ADS is purpose-built for containers and microservices-based application architectures and elegantly integrates with DevOps processes.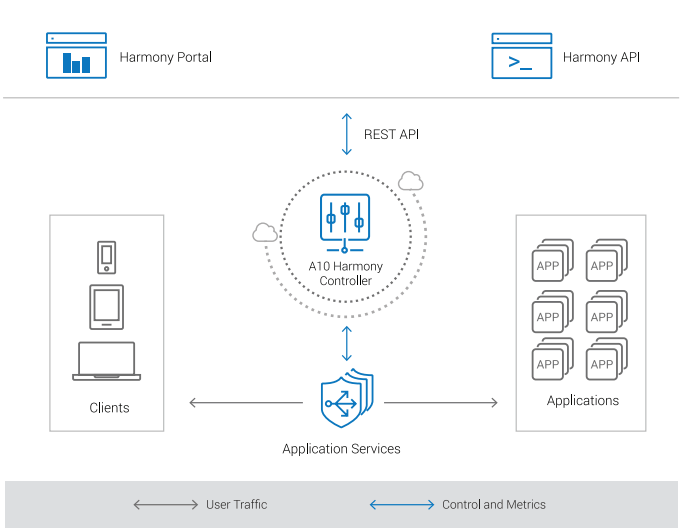
The unified nature of Lightning ADS is shown here. Lightning ADS has built-in elasticity and WAF to maintain application availability and security. It also comes with integrated, rich analytics to let you quickly understand your application’s performance and security posture so you can take immediate action if there is an anomaly.
When to Act
A small volume of malicious traffic is always mixed in with normal traffic. The application security policies of Lightning ADS takes care of those. However, when the amount of malicious traffic goes beyond that “normal” threshold, it is time to take action.
You can configure alerts via the A10 Harmony Portal or through APIs so you receive a notification when the number of WAF related events exceeds these normal limits.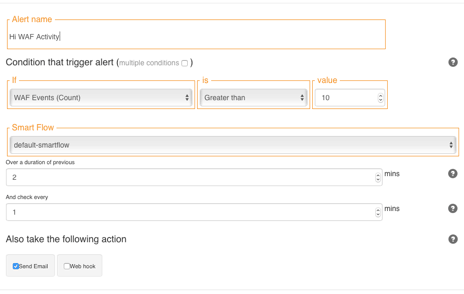
Identify the Attacker
When you receive the alert, the WAF should be working and stopping the attacker from stealing any data. Meanwhile, the elasticity of Lightning ADS will trigger and you may incur additional costs. It is important to quickly identify the attacker and block them from sending further requests.
Traditionally, finding the attacker’s IP address required filtering and analyzing the logs for a signature. But because analytics is an integral part of Lightning ADS, you can find an attacker’s IP address automatically. The IP addresses of top attackers and information regarding the number and type of malicious requests they are sending is listed as a table in the security dashboard of the Harmony Portal.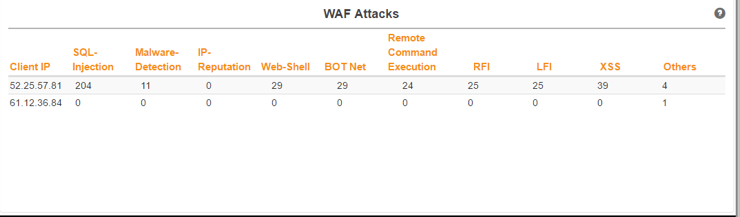
Before blocking a client, it’s critical to be sure that traffic is really coming from an attacker and that it’s not a false positive. That is why the Harmony Portal takes you one level deeper and displays a list of logs from the selected client with full information that categorizes the requests as malicious.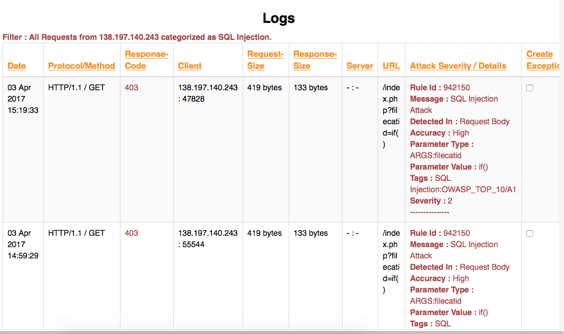
Block the Attacker
Lightning ADS providers an access policy for black listing specific IP addresses or subnets. Setting up a deny rule for the identified IP address will start blocking all traffic from that client without spending the resources required for DPI. This frees up resources for Lightning ADCs.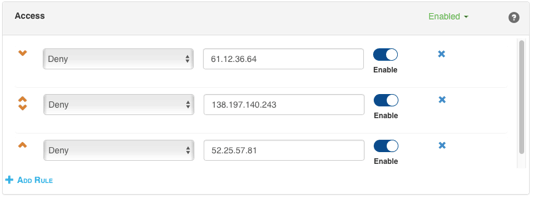
Another way to bring costs down further is to block traffic from the attacking client in the IP firewall. When the IP firewall blocks traffic, it doesn’t reach the Lightning ADC and resource utilization is reduced. In this case, the A10 Harmony Controller scales in the ADCs by removing some of the instances, which brings down the cost.
For a step by step guide to identifying and blocking an application attacker, follow along with this video:
If you come from a NOC or SOC background, and think this sounds too good to be true, we encourage you to give A10 Lighting ADS a try and experience the benefits for yourself. Simply fill out the request form for a free 30-day trial and A10’s customer success team will help you onboard your application and get you up and running Lightning ADS.
Seeing is believing.
Schedule a live demo today.