The Evolving Landscape of Service Provider Security

Protecting only the Gi Interface is no longer enough
Mobile networks are evolving quickly, and with change comes vulnerability.
Until recently, the Gi-LAN connecting the (Evolved Packet Core) EPC to the internet was considered to be the most vulnerable part of the service provider network and was protected via Gi-Firewal and anti DDoS systems. The rest of the EPC links were considered difficult targets for hackers because advanced vendor-specific knowledge was required for a successful attack. Since the typical hacker prefers a soft target, defensive measures weren’t a priority for developers or carriers. Network complexity was a defense in itself.
However, the requisite know-how to attack EPC from other interfaces is now becoming much more common. The mobile endpoints are being infected at an alarming rate, and this means that attacks can come in from the inside of the network. The year 2016 saw a leap in malware attacks, including headline-makers Gooligan, Pegasus, and Viking Horde. Then the first quarter of 2017 saw a leap in mobile ransomware attacks, which grew by 250 percent.
The need for securing the EPC is tied to advances like LTE adoption and the rise of IoT, which are still gaining speed. LTE networks grew to 647 commercial networks in 2017, with another 700 expected to launch this year. With the adoption of LTE, IoT has become a reality—and a significant revenue stream for enterprises, creating a market expected to reach $561.04 billion by 2022. The time to take a holistic approach to securing the service provider networks has arrived.
Data Paths to Mobile Service Providers
There are three primary data paths connecting mobile service providers to the outside world:
1. A link to the internet through S/Gi LAN
2. A link to a partner network to serve roaming users
3. A link for traffic coming from towers
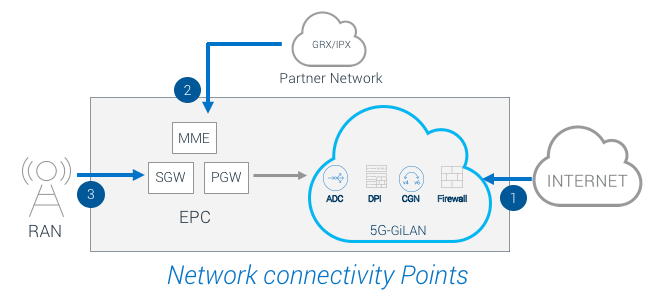
The security challenges and the attack vectors are different on each link. Until recently, the link to the internet was the most vulnerable point of connectivity. DDoS attacks frequently targeted the service provider’s core network on the Gi Link. These attacks were generally volumetric in nature and were relatively easy to block with highly scalable firewalls and DDoS mitigation systems.
The Expanding Attack Surface
The threat landscape is rapidly changing and attacks can come from other points of connectivity. This has been theoretical until recently; while numerous academic research papers have been published in the past decade suggesting that attacks from partner networks or radio access networks (RANs) were a possibility, those threats are no longer merely an intellectual exercise: they are real. At the same time, the rapid rise of IoT is exposing the threat of malicious actors taking control and weaponizing devices against a service provider.
Multiple botnets, such as WireX and its variants, have been found and taken down. So far, these attacks have targeted hosts on the internet, but it’s just a matter of time until they start attacking Evolved Packet Core (EPC) components.
There are multiple weak points in EPC and its key components. Components that used to be hidden behind proprietary and obscure protocols now reside on IP, UDP, or SCTP, which can be taken down using simple DoS attacks.
The attack surface is significantly larger than it used to be, and legacy approaches to security will not work.
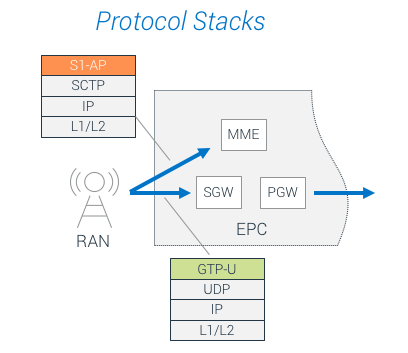
A DDoS Attack, like a signaling storm, against an individual entity can be generated by a malicious actor or even a legitimate source. For example, a misbehaving protocol stack in an IoT device can cause an outage by generating a signaling storm.
How A10 Can Help in Securing the SP Network
A10 Networks products defend some of the world’s largest telecom providers. Thunder® Convergent Firewall (CFW), our S/Gi Firewall solution has been protecting large Tier 1 and Tier 2 operators, and our DDoS protection solution, Thunder CFW, has been deployed by many large service providers and public cloud infrastructures. These solutions can easily mitigate multi-terabit attacks.
Now our offerings can do an even deeper packet inspection and advanced correlations at scale.
A10’s Comprehensive Security Solution for EPC
- Stateful inspection
- We maintain stateful sessions for GTP, SCTP, and other related protocols to ensure that messages follow a standard path. Script-kiddies will no longer be able to easily generate simple flood attacks against your network.
- Protocol conformance
- We inspect the flow and ensure that incoming messages conform to standards and all mandatory attributes are present.
- Filtering
- We have extensive filtering capabilities that can filter on message length as well as message fields. We can do deeper inspections and filter on information elements including IMSI and APN. In short, we have full visibility into the message so we can filter on any field of the message and block it.
- SCTP NAT’ing
- We can NAT outbound SCTP protocol through GRX networks. This creates security through obscurity by hiding the internal network details.
- Protection against signaling floods
- Signaling floods can be detected with deep packet inspection capabilities. For example, a flood of PDP-Create or PDP-Delete requests coming in from a single source can be rate limited
With these powerful tools, we can detect and mitigate, or stop, a number of advanced attacks specifically against EPC. We can also do a granular deep packet inspection to protect against user impersonation by means of spoofing, network impersonation, and signaling attacks. We understand and can parse all versions of GTP control protocols, SCTP, and Diameter.
To summarize, in addition to mitigating and stopping terabit-scale attacks coming from the internet and providing stateful firewall services, A10 Networks is now upping the ante and can provide full-spectrum security for service providers to protect other connected links.
Learn more about A10’s service provider solutions.
Seeing is believing.
Schedule a live demo today.