What is a DDoS Attack; Distributed Denial of Service Attack?
DDoS Attack Definition
A Distributed Denial of Service cyberattack, otherwise called a DDoS attack, is an assault on an online service that is, unfortunately, remarkably easy to mount and, if your cybersecurity team doesn’t have effective DDoS protection tools, these attacks are hard to counter.
The simple answer to “what is a DDoS attack?” is that it’s a type of cyberattack that’s intended to reduce or remove the performance of an online service. How a DDoS attack is put into motion is, at least in concept, also simple: By sending specially crafted requests from a network of compromised devices controlled by hackers—called a “botnet”— the target device, for example, a web server, becomes overwhelmed and connections from normal traffic get slowed down or even excluded while the computing resources of the target (processor cycles, network interfaces, memory used for communications processing) become exhausted. At best, a small Distributed Denial of Service cyberattack will cause a significant slowdown in the service’s response to valid clients while, at worst, a large-scale botnet attack can effectively take an online service out completely.
How easy is it to mount a Distributed Denial of Service Attack? There are tools that are so easy to find and deploy that a child could do it. Moreover, there are hackers out on the dark web offering what has been called “DDoS as a service” who will launch a DDoS attack for anyone for prices as low, according to the Dark Web Price Index 2022, as $200 for targeting a DDoS-protected website with 20,000 to 50,000 requests per second for 24 hours. A DDoS cyberattack of 10,000 to 50,000 requests per second on an unprotected website is priced at only $10 for one hour.
Inside a Botnet Attack
Over the last few years, the number of botnets used for launching DDoS attacks has increased dramatically as has their size. The Mirai botnet, which primarily targeted online consumer devices such as IP cameras and home routers, was released as open source code in 2016 and used that same year to knock security journalist Brian Krebs’ website offline with an estimated 620 gigabits of traffic per second. At the time this was the biggest DDoS attack ever seen but it was dwarfed by a subsequent attack on internet DNS service provider Dyn. This botnet attack was driven by something between 800,000 and 2.5 million infected devices that generated a load that ranged between 700 to 800 gigabits per second and occasionally rose to over one terabit per second. While Mirai appears to be the largest botnet attack discovered to date, a variant called Mirai Okiru has the potential to co-opt a staggering 1.5 billion IoT devices.
Types of Distributed Denial of Service Attacks
There are many types of DDoS attacks, which can be broken down into three major cyberattack groups: volumetric attacks, protocol DDoS attacks, and application layer attacks with some assaults combining features of more than one group.
Volumetric Attacks
The most common DDoS attack are volumetric attacks, also known as “flood attacks.” The goal is to overwhelm the target by sending huge amounts of traffic so that wanted traffic is excluded; in other words, volumetric attacks clog up the pipes. A traffic increase that lasts over a long period or a change in website metrics (reduced sales or reduced user interaction) can be indicators that a volumetric attack is in progress. Volumetric attacks can also be low-level events that simply degrade bandwidth rather than blocking all normal traffic. Given the high cost of losing business compared to the very low cost of mounting a volumetric DDoS attack, this version of cyberattack can be very expensive for the attacked organization.
Protocol DDoS Attacks
In protocol DDoS attacks, network protocols at OSI Layers 3 and 4 are exploited in an attempt to deny service. Some of these attacks rely on normal protocol behavior and simply exhaust resources while others leverage weaknesses that are inherent in the communications architecture. The first indications of protocol DDoS attacks are unusually high processor utilization and specific computing resources running low. Again, just as with low-level volumetric attacks, low-level protocol DDoS attacks can be costly and hard to identify.
Application Layer Attacks
Rather than overwhelming networking resources, application layer attacks (OSI Layer 7) exploit weaknesses in things such as web servers and web applications and their platforms. These are also called web application vulnerability attacks. By interacting with specific code targets with known vulnerabilities, aberrant behavior (reduced performance or outright crashing) is invoked. Detecting these application layer attacks can be very difficult because they usually don’t involve large traffic volumes so finding the problem source can be difficult.
Old vs. New DDoS Attacks
To illustrate how DDoS attacks work, we’ll look at two specific examples: The SYN flood DDoS attack, which is arguably the oldest and one of the simplest, and NXNSAttack, one of the newest and more technically complicated.
SYN Flood DDoS Attack, a Classic Distributed Denial of Service Attack
One of the oldest types of distributed denial of service is called a SYN flood attack and is a combination of a volumetric attack and a protocol attack. In a SYN flood a particular type of TCP data packet, a SYN packet, is sent to the target requesting a connection usually with a fake sender’s address, also called a “spoofed” address. The target replies by sending an acknowledgement back to the requestor, called a SYN-ACK to the given sender’s address.
With a normal connection request, the requestor would then reply with an ACK but in a SYN flood attack there’s no response either because there’s no device at the given address or, if a device is there, it knows it never sent a SYN request to the target and, therefore, doesn’t respond. When there are a few of these fake SYN requests hitting a target it’s unlikely to be noticed but at some higher level, the target’s performance becomes degraded. When there’s a large-scale attack, the target is usually completely overwhelmed. While a SYN flood launched from a single computer is easily filtered out, a distributed SYN flood attack generated by hundreds of thousands or even millions of machines co-opted into a botnet is far more difficult to mitigate.
NXNSAttack, a New Distributed Denial of Service Attack Via DNS
New exploits and vulnerabilities in computer systems and networks are found with increasing regularity and they become the basis for new attack vectors. In late May 2020, cybersecurity researchers in Israel disclosed a attack called NXNSAttack which relies on a vulnerability in the Domain Name System (DNS) where recursive DNS servers pass DNS queries to upstream authoritative servers. These servers can delegate queries for domains they can’t resolve to other DNS servers controlled by threat actors. It is this delegation process that can be abused to launch DDoS attacks. The result is a simple DNS query can be amplified up to 1,620 times crashing the DNS servers that are authoritative for a target, thereby preventing the target from being resolved and effectively knocking it off line.
Learn more about what’s so bad about the NXNSAttack DNS Amplification Attack
Who Will Become a DDoS Cyberattack Target?
As the internet becomes more complex and the devices and botnets become more numerous, it’s guaranteed that DDoS attacks will become more aggressive and more frequent. As a result, the cost of botnet-driven cyberattacks to businesses will escalate and it’s not just big businesses that will suffer; SMBs are already hot targets for attacks.
Over the last few years there has been a rise in cases where companies have been threatened with DDoS attacks unless a ransom is paid. These are called RDoS attacks and experts predict this trend will continue. According to Cloudflare: “In Q4 [2021], ransom DDoS attacks increased by 29 percent YoY and 175 percent QoQ [and in] December alone, one out of every three survey respondents reported being targeted by a ransom DDoS attack or threatened by the attacker.”
You may discover that when you go to senior management looking for more funding to bolster your cybersecurity defenses for better DDoS protection, you’ll probably be asked “what is a DDoS attack?” and while the technical details may cause the CEO’s or CFO’s eyes to glaze over, the financial consequences of inadequate DDoS attack defenses should make them sit up straight. Here are some of the facts about what a distributed denial of service attack could cost your organization:
- The “Cost of a Data Breach Report 2021” from the Ponemon Institute found that the average cost of a data breach was $4.24 million with healthcare breaches being the costliest at $9.23 million
- The same report also found that the average time taken to identify and contain a data breach was 287 days and a breach lasting under 200 days costs 30 percent less than one that lasts longer than 200 days.
- In late 2021, more than 100 firms were threatened with DDoS attacks unless they paid a ransom
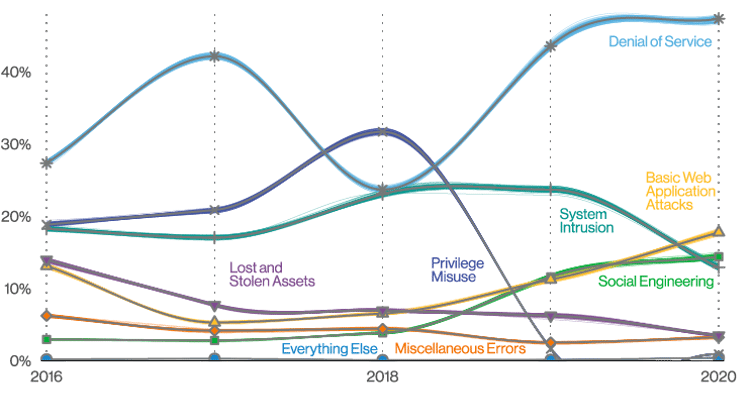
Patterns over time in incidents from Verizon’s 2021 Data Breach Investigations Report
You might also point out that while serious enterprise cybersecurity is expensive, a lack of serious enterprise security can be even more expensive. Now is the time for your cybersecurity team to start making plans to protect your organization from the next DDoS attack.
How Can A10 Help?
Even though new types of DDoS attacks appear frequently, the A10 Defend suite employs advanced defense strategies that protect against all kinds of cyberattacks including new, novel DDoS attacks that could bring down your DNS services. Visit A10’s DDoS Protection solution page to learn more.