The Not-so-Hidden DDoS Arsenal Knocking at Your Network Door

It’s become the norm to see Denial-of-Service (DoS) and Distributed DoS (DDoS) attacks take high profile targets off-line appear regularly in the news headlines. Take the recent attacks on gaming networks by the Lizard Squad affecting “Destiny” and “Call of Duty: Ghosts” in September, the 400 Gbps attack reported by CloudFlare in February 2014, and the very high-profile financial company attacks of 2013 by Cyber fighters of Izz Ad-Din Al Qassam, just to name a few. Looking at these attacks begs the question how easy is it to launch an attack today? What new attack tools and threats are emerging? By looking at this we can effectively evaluate solutions to mitigate the problems.
First, how can a DDoS attack be launched? Unfortunately, generating attacks has never been easier, and tools are well publicized. Toolkits can be downloaded directly from the Internet, just like your favorite iPhone or Android app. Many of the toolkits even have easy to use GUIs to “point and click” an attack with ease, many have different choices of attacks from the same tool. For example, LOIC offers both the simple, but still frequent, network level SYN flood attack and the more advanced application level HTTP flood attack. Other easy to use attack tools include Dirt Jumper, Darkness (Optima), HULK, BroDos, LOIC, HOIC, and many more.
While regular toolkits have been around for many years, we do see an evolution, a quite natural evolution, to smartphones as a compute platform to launch an attack. These are in the wild today, they are not like apps; they are apps. Oft cited tools for Mobile DDoS attacks include MobileLOIC and AnDOSid. What is interesting with these tools is not just that a phone can now launch a cyber-attack (for their processors are still slower than most PCs), but the sheer number of devices that could be weaponized for a DDoS attack.
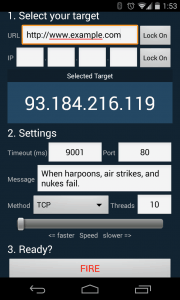
DDoS: There’s an app for that. MobileLOIC Android interface
PC and phone based tools can launch thousands of attacks per second, but where it can get to website Armageddon status, is when these individual instances function together, as a botnet, effectively networking together to function as one, amplifying the attack potentially thousands of times or more. Going back to the phone example, when we consider there are 6.8 billion phones world-wide, even a fraction of compromised devices could potentially result in a significant force to knock out a website or other resource.
Botnets themselves can be formed from malware compromised individual machines, reporting to a central location for orders, IRC servers have been shown to be an effective proxy for hackers to relay orders to bots that check in.
On the commercial side we have seen DDoS for hire emerge, sometimes coined as DDoS as a Service (DDoSaaS). Known as “stressers” or “booters”, these websites offer low cost attacks on demand to “Stress Test” a website, all controlled by easy to use web pages. In this scenario, you wouldn’t even need to install any software. Payment in this scenario can also be anonymous; the mainstreaming of Bitcoin helps the perpetrators pay with an alternative to tracked regular financial payment mechanisms.
Toolkits, mobile DDoS attack apps, and DDoS for hire, are all available today and generally available. A cursory Google search is the doorway to any network newbie, or gamer n00b, becoming capable of stressing or downing a website. Today it is more critical than ever to ensure defenses are in place. In my next A10 Networks DDoS blog we’ll look at a number of newer attacks that how the advance in DDoS attack types beyond the basic network floods of old.
Seeing is believing.
Schedule a live demo today.