DDoS Threat Intelligence Map from A10

Data is not a defense. You need actionable intelligence.
Security researchers are swamped with massive volumes of data created during attempted attacks every day. But raw data cannot be used to develop an actionable defense until it is put into context and transformed into useful intelligence.
Threat intelligence combines the information acquired from the repeated use of attacking agents with the knowledge gleaned from millions of vulnerable IP addresses and hosts. Security researchers use this intelligence to proactively improve DDoS defenses.
Maps of the past are no help. This map shows the future.
A10 has created the DDoS Threat Intelligence Map to help you visualize the DDoS threat landscape and prepare for the next wave of DDoS attacks against your infrastructure.
Unlike the attack maps already on the internet that only show attacks that have already happened, A10’s DDoS map give you insights into where the next DDoS attacks will come from. By combining this knowledge with A10’s actionable DDoS threat intelligence platform, Thunder TPS, you can take a proactive approach to DDoS protection.
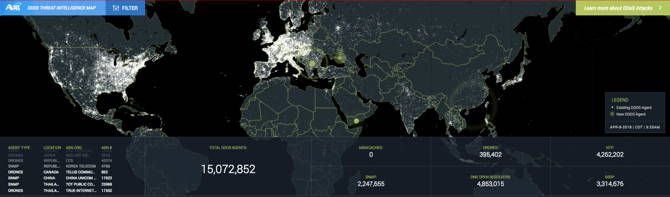
A10’s DDoS Threat Intelligence Map
What can you learn from the DDoS Threat Intelligence Map?
We all wish we could predict the future, but you may not know why or when a DDoS attack is going to come. You just know that it will come. By knowing where the weapons are, you can build a more effective defense. A10’s DDoS Threat Intelligence service, powered by A10 Research and ThreatSTOP, identifies millions of IP addresses commonly used as agents for DDoS attacks.
Unlike legacy DDoS defenses that only support thousands of blacklist entries, A10’s map includes large class-lists of threat objects with millions of entries that can be dynamically updated to make threat intelligence proactively actionable. This threat intelligence includes IP addresses of reflection attack agents, sprawling IoT botnets, and DDoS botnets actively used in the last 24 hours.
You can choose the categories of attack agents that you want to view, such as DNS or drone agents, see the geolocation of potential attacking elements, and check out entries that have been newly identified or deprecated from the snapshot of the near real-time DDoS threat feed.