Insight Into the DDoS Attacks on the French Government

The attacks are ongoing as of this writing. Here are a few screenshots of data and some insight. I’ll make sure to keep it brief since you have seen this news in various outlets.
Our sensors began receiving attack traffic at 18:00 GMT Sunday, beginning with an ARD/ARM attack and gradually ramping up a much larger SSDP amplification attack.
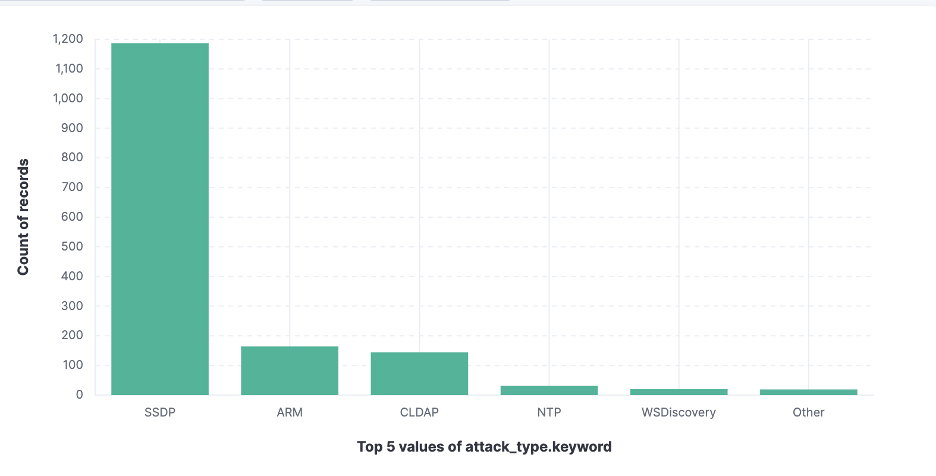 Attack Types Destined for France Starting at 18:00
Attack Types Destined for France Starting at 18:00
Diving into the SSDP data, we see:
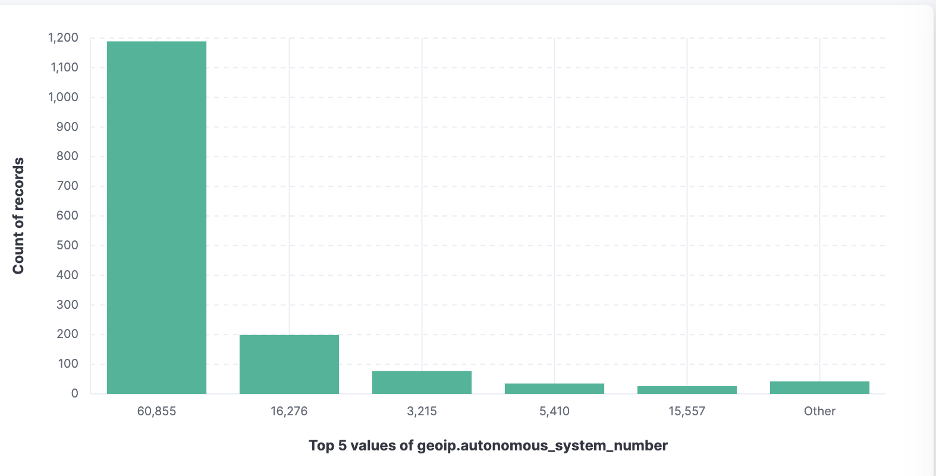 Top-5 French ASNs seen during this period
Top-5 French ASNs seen during this period
Within AS 60855, we begin to see the dynamics of the attack: 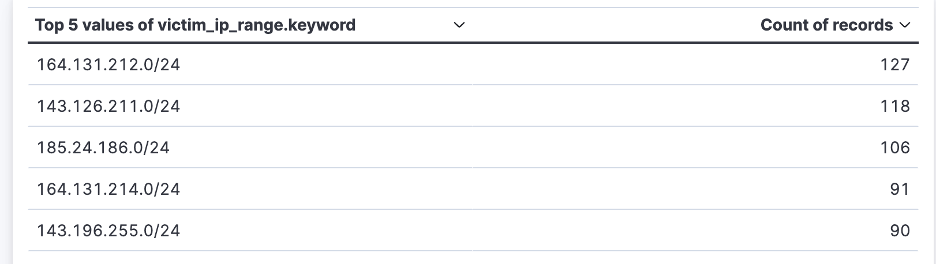 Top-5 subnets under attack within ASN 60855
Top-5 subnets under attack within ASN 60855
Digging deeper into a sample of this attack, one can see that one of the destinations rests within this subnet. “social.gouv.fr”
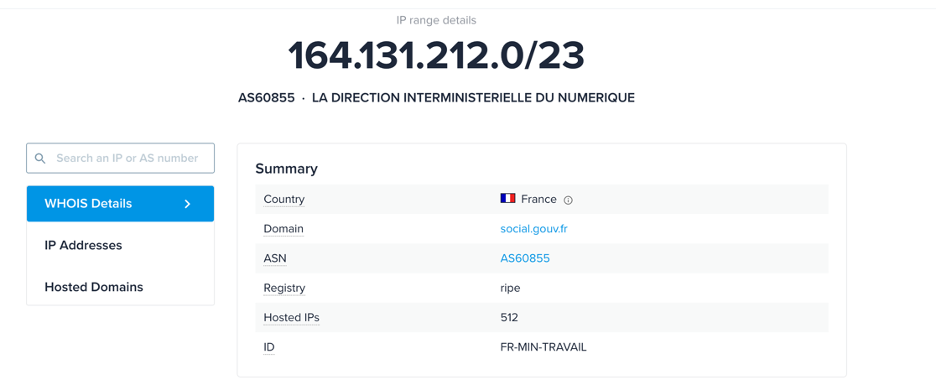 Details on the subnet from ipinfo.io
Details on the subnet from ipinfo.io
Using our product A10 Defend Threat Control, you can look a bit deeper, still examining a high-level view of attacks on the entire ASN and its carpet bomb nature.
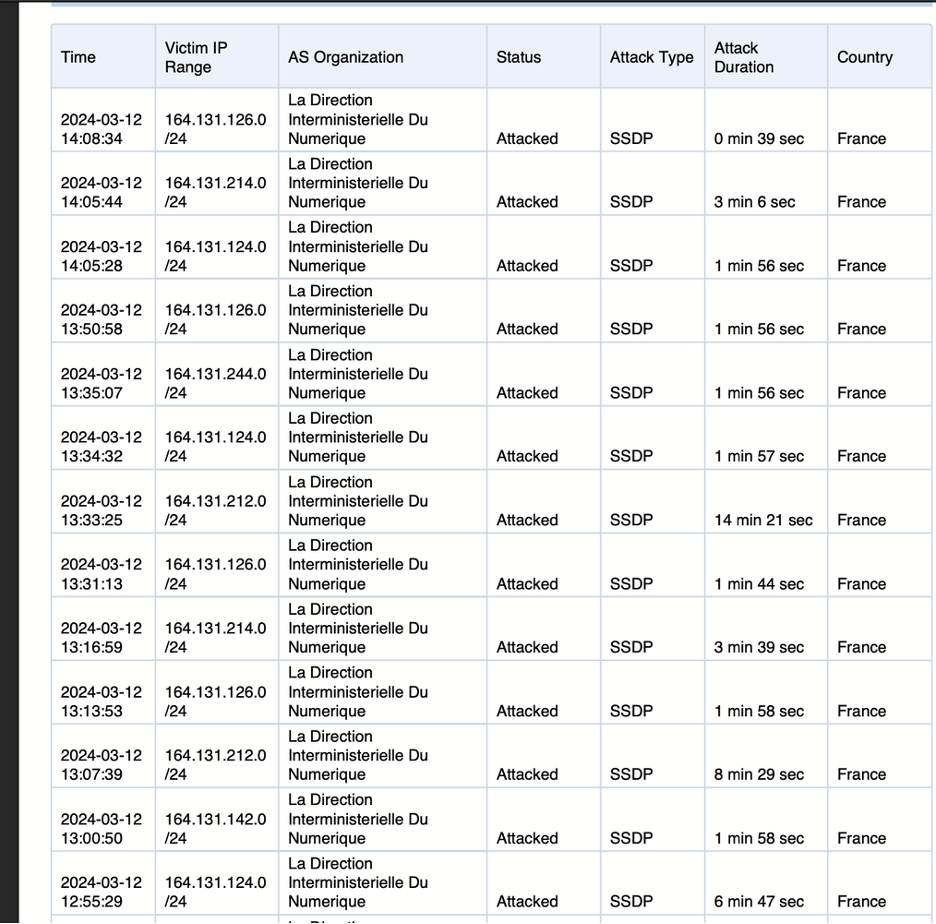 Snapshot from a Threat Control report for ASN 60855
Snapshot from a Threat Control report for ASN 60855
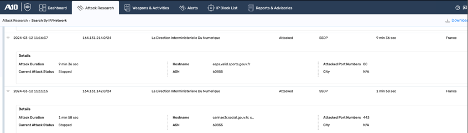 Threat Control snapshot showing attacked ports and hostname samples
Threat Control snapshot showing attacked ports and hostname samples
So, the attack packets will be sourced from various ports. Theoretically, if the SSDP device works correctly, you will see an attack packet sourced from UDP port 1900, destined for UDP port (in this case) 80 or 443, and likely meant to find its way through the path’s myriad ACLs and firewalls. However, some packets will be sourced from UDP high ports and destined for ports 80/443. It is easier to tell the difference between this packet and Quicc when under stress if you read the payload.
From our experience, SSDP amplification attacks carry a UDP payload of 360 bytes or more. Depending on the number of reflectors in use this could turn into a very large attack.
Originally posted on LinkedIn by the author.
See press coverage of the ongoing attacks.