How to Defeat Emotet Malware with SSL Interception

One of the longest-running and more lethal malware strains has once again returned on the scene. Called Emotet, it started out as a simple banking Trojan when it was created in 2014 by a hacking group that goes by various names, including TA542, Mealybug and MummySpider. Emotet malware is back in the headlines and continues to be one of the most significant threats facing companies today.
What is Emotet Malware (a.k.a. Emotet Trojan) and is it a Threat?
Its history is long and varied as you can see from the below timeline:
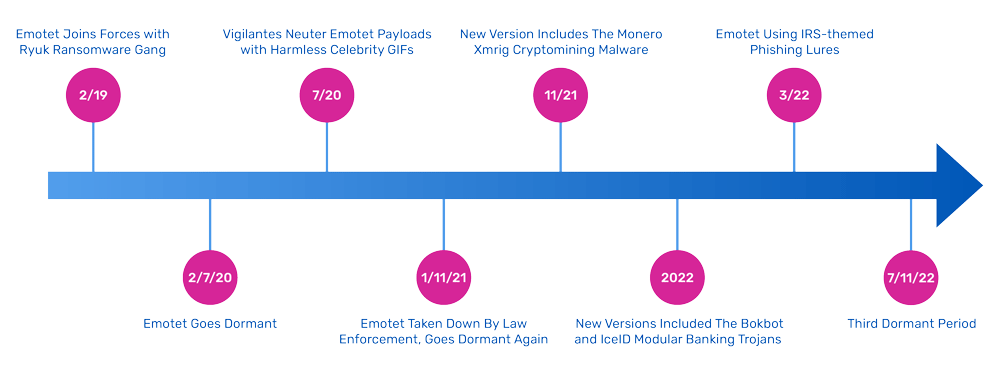
Before going dormant during three periods starting in 2020, the Emotet botnet had been the world’s largest and most active cybercrime operation, with Any.run awarding its top spot, in terms of number of endpoints attacked, in 2019 and 2020.
Avoiding Emotet malware will require various tactics, including deploying SSL decryption and SSL inspection across your network and adopting Zero Trust security models to provide better protection. If you needed any additional encouragement, the U.S. Department of Defense recently extolled the advantages of adopting a Zero Trust security model for its own networks.
Dormant Periods for Emotet Malware
There were various reasons for why Emotet malware attacks stopped sending out phishing lures and went dark: Several researchers suggest the Emotet malware group went through a change of management in 2020, and perhaps again in 2021 after a combined law enforcement operation took down most of its infrastructure.
The dormant periods could also be explained as periods to recode particular modules, posited Darren Guccione, co-founder and CEO of Keeper Security. He was quoted in The Register: Emotet “could be developing new malware or trying a different business model. It appears developers are trying to deter researchers as the group improves their malware in order to stay one step ahead in a continuously evolving threat landscape.”
How Does Emotet Work
Emotet has three things that make it more lethal. First, it continues to use well-crafted obfuscation methods. It was one of the early malware samples to deploy polymorphic code to vary its size and attachments, meaning that it would change its form and procedures to try to evade detection. Other techniques used multi-state installation procedures, encrypted communications channels and migrated its 32-bit code to 64-bit. Over the years, it has had some very clever lures, such as sending spam emails containing either a URL or an attachment, and it purports to be sending a document in reply to existing email threads. IBM’s X-Force found one variation that uses the COVID-19 virus as part of its phishing lure. These lures are often sent in various languages native to the intended targets, producing not only English but German, Chinese and Spanish versions.
Secondly, Emotet has a well-integrated collection of crime methods. Intel 471’s 2022 Cyber Threat report says, “The novelty of Emotet operations resides in the fact that the operators do not need to entrust its malware attack and delivery to another group nor buy installs. Their own capabilities enable them to grow the botnet by taking advantage of the infections they already have.”
Finally, what makes Emotet such a threat is that its developers are continually making modifications to its code, changing its tactics and increasing the level of obfuscation it employs. The Emotet trojan evolved quickly into a series of botnets that would help launch additional phishing attacks. Bromium’s researchers in 2019 documented how Emotet shifted its tactics from stealing bulk data to selling their malware as a service for others to ply their trade. Back then, Emotet joined forces with the Ryuk ransomware group. Researchers have found that the November 2021 version includes the Monero XMRig cryptomining malware and new reconnaissance features and commands. And more recent 2022 versions included the BokBot, Bumblebee and IceID modular banking trojan that uses infected Microsoft Word macros and were using the mobile malware Mailbot. Lately, Emotet is using a compromised Windows .LNK file attachment which sets off a series of Powershell commands that downloads its malware.
Emotet Malware’s Offensive Measures
Because Emotet was so popular and dangerous, it motivated many offensive measures to fight its cyberwar of crime. Back in February 2020, Binary Defense developed two versions of a killswitch exploiting different weaknesses found in Emotet’s code. Eventually, the Emotet developers figured this out and updated thecode to get around the killswitch, showing how active Emotet’s developers are.
In 2021, a group of whitehat vigilantes neutered about a quarter of all Emotet downloads, substituting the malware with harmless animated celebrity GIFs. The ZDNET post linked above walks you through how the vigilante was able to modify the Emotet malware and make the substitution. The vigilante’s identity remains unknown, although some researchers, who go by the name Cryptolaemus, which is a reference to a particular insect, have speculated it could be a rival malware group.
The MS Office macro infection vector got to be so pervasive that in October 2021 Microsoft took the step of blocking macro execution by default from files downloaded from the internet. This motivated the Emotet creators to use other tactics, such as saving their attachments to cloud drives, using HTML applications and shortcuts to evade this protection.
Start with These Malware Protection Strategies
The U.S. CISA issued an alert in January 2020, which describes various tactics that you can use to try to steer clear of Emotet’s evil intent and move towards a more effective Zero Trust security model. This includes adding group policy objects and firewall rules to block it along with proper network segmentation and using mail authentication technologies such as DMARC and SPF on your corporate domains. Because today’s Emotet email campaigns use stolen email reply chains to distribute malicious Excel attachments, it also helps if you can disable Word and other Office macros from automatically executing from email attachments. This is a common malware trick not exclusive to Emotet. You can safely open these documents in Google Docs as an alternative, and Bleeping Computer has other instructions to help avoid activating these malicious attachments.
View into Encryption Blind Spots with SSL tools
Malware attacks such as Emotet often take advantage of a fundamental flaw in internet security and leverages organizations that haven’t yet adopted a Zero Trust security model. To keep the remaining active Emotet botnets—and countless other cyberthreats—out of their environment, organizations need to rely on more robust and reliable measures based on SSL interception (SSL inspection) and SSL decryption. This practice is highly effective for identifying SSL traffic to prevent spoofing, man-in-the-middle attacks, and other common exploits from compromising data security and privacy. Unfortunately, it also creates an ideal hiding place for hackers. But since more than half of the malware attacks seen today are using some form of encryption, this creates blind spots where malware can elude SSL traffic-based defenses.
The most obvious way to address this problem would be to decrypt traffic as it arrives to enable SSL inspection before passing it along to its destination within the organization—an approach known as SSL interception. But here too, problems arise. For one thing, some types of data aren’t allowed to be decrypted, such as the records of medical patients governed by privacy standards like HIPAA, making across-the-board SSL decryption unsuitable. And for any kind of traffic, SSL decryption can greatly degrade the performance of security devices while increasing network latency, bottlenecks, cost, and complexity. Multiply these impacts by the number of components in the typical enterprise security stack—DLP, antivirus, firewall, IPS, and IDS—and the problem becomes clear.
How A10 Networks’ SSL Inspection Product Helps
A10 Networks Thunder® SSL Insight (SSLi®) eliminates the SSL encryption blind spot to enable effective SSL interception and assemble a more effective Zero Trust security model. Instead of relying on distributed, per-hop SSL decryption, organizations can use a single Thunder SSLi solution to decrypt traffic once, allow SSL inspection by as many separate security devices as needed in tandem, and then re-encrypt it once on the way out of the network. To ensure regulatory compliance, the solution also allows SSL decryption policies to selectively bypass traffic for specific web pages and domains while making sure that everything else is decrypted.