Effectively Inspecting and Blocking Malicious Traffic

Take a moment to imagine this scenario: Your company is going about its business, when, by a stroke of “luck”, someone notices signs of malicious activity on the network. However, the security devices you have deployed in your network fail to report any active threats and you have no idea how to track down what’s going on. Since your security devices can’t decrypt malicious traffic, they remain blind to hidden threats and never find the source of the problem.
By the time you realize this, it’s too late: Encrypted malware has made its way into your infrastructure, and it’s no longer a matter of prevention, it’s a matter of mitigation and damage control.
For some companies, this hypothetical situation is all too real and there’s usually a combination of problems at play, rather than a single culprit.
Here, we’ll look at some of the problems contributing to companies’ inability to inspect malicious traffic effectively, as well as the best solutions to these problems.
Problem 1: An Encrypted World
Encryption is now nearly ubiquitous: More than 80 percent of internet traffic is already encrypted, according to Google’s Transparency Report.
Although increased encryption is good news in terms of data privacy, it also introduces a security “blind spot” that your network defenses cannot look in to. Unfortunately, hackers wasted no time in learning how to exploit this blind spot and have started using it for the delivery of their malware and other malicious content.
Many companies rely on their existing security solutions and try to leverage their built-in decryption capabilities, if available, but this comes with its own set of disadvantages: These types of “bolted-on” decryption tools, commonly implemented as mere software extensions, result in a significant amount of performance degradation.
Testing carried out by NSS Labs revealed just how much performance suffers during the encryption process:
- Average throughput clocked in at 60 percent
- Connection rates dropped by 92 percent
- Application response time latency jumped by 672 percent
This means that, for example, a security solution that originally offers 10 gigabytes of inspection throughput might be limited to a mere 2 or 3 gigabytes once it starts decrypting. That’s a staggering 70-80 percent performance drop.
We have covered this topic in detail on the blog post, “Next Generation Firewalls May Not Stop Malware.”
To prevent such extreme performance degradation, some companies turn to dedicated decryption solutions. While such solutions are certainly the perfect remedy to all their decryption woes, they can sometimes prove to be overly complicated and difficult to deploy. That’s why companies need to seek out dedicated decryption tools that are not only effective at eliminating the blind spot, but also easy to deploy and use.
Problem 2: An SSL Inspection Strategy That Is Scalable With Growth?
With a dedicated decryption solution, a small company can easily gain full visibility into its network traffic, encrypted or not, and can defend against all sorts of attacks. However, this solution is effective only if deployed in a single location with a localized security stack requiring the decryption.
As your company grows to include multiple branches and offices it will undoubtedly run into problems as the scope of the need for decryption and overall visibility expands. That’s because, without centralized visibility, organizations are unable to see the bigger picture. Instead, they’re stuck with a disconnected and incomplete view of all their data, looking at one branch or office at a time.
For example, a large organization might have its IT department located in its main headquarters. However, the IT team is going to need to take a closer look at all of the organization’s traffic, including the traffic flowing through the different offices and branches around the state, country or world. Only then would they be able to make sense of it all.
To solve this issue of disconnected and localized visibility, companies need to employ a centralized management and visibility solution, complete with intuitive dashboards and actionable analytics, that can manage and control all multi-site deployments, regardless of geographic location.
Additionally, centralized policy management can ensure that security policies remain consistent across all deployments. Consistent policies can, in turn, help organizations stay compliant with a variety of privacy and data standards across the board.
Problem 3: Modern Apps Create New Problems
With the rapid adoption of SaaS technologies and the move of traditional productivity tools to the cloud, many organizations can’t even imagine functioning without G Suite, Dropbox or Office 365, and rightfully so.
However, companies increasingly employing the use of SaaS applications means that the applications previously hosted on-prem are now being accessed in the cloud. This has increased the volume of “north-south” traffic between the enterprise and the internet, as opposed to the previous model of “east-west” traffic flow, where applications were accessed within the network. Regardless of the traffic flow however, you still expect the user experience to be as if the applications are being accessed locally.
Since legacy security solutions weren’t designed to handle such unprecedented volumes of traffic at the perimeter, they can face performance degradation and introduce bottlenecks. While such a slowing down of the network might be acceptable in some cases, in the case of SaaS applications, it can create huge problems because it can severely degrade the user experience.
To avoid such problems and to maintain a smooth user experience, many SaaS providers recommend that companies allow their application traffic to circumvent their security products and quickly pass through to the trusted cloud service, for example Microsoft and Office 365. However, doing so creates a huge gap in overall traffic visibility as now you don’t have access to your SaaS traffic and statistics.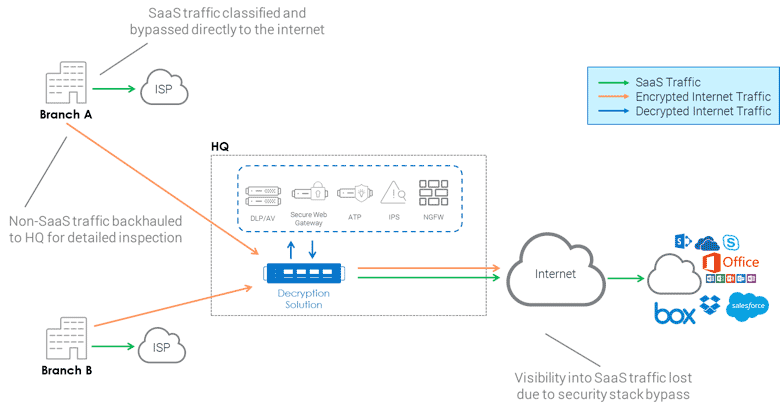
The lesson here is that disconnected and localized network visibility isn’t enough on its own, especially in the age of SaaS. Companies need to be able to see into their cloud traffic and deployments. They can accomplish that with a localized, dedicated decryption solution that works hand-in-hand with a centralized management and visibility solution that’s able to log traffic both in the network and the cloud.
Delivering Intelligent Solutions for Local Decryption and Global Visibility
To recap, you need intelligent security solutions that compliment your existing security deployments and help you overcome security scale and performance as well as overall visibility issues:
- A dedicated decryption tool that’s easy to deploy, user-friendly and supports your entire security infrastructure within your enterprise network. This way, one decryption tool can serve your entire security stack, thereby reducing total cost of ownership (TCO).
- Centralized policy management so that your organization can have uniform security policies applied across all deployments.
- Actionable analytics, and centralized application visibility and control to provide your company with application level visibility and control for both, network and SaaS traffic.
- Centralization of management and visibility will enable your organization to catch any traffic abnormalities that would otherwise be lost due to isolated analytics at each site.
Between widespread encryption, multiple geographically distributed locations, and a wealth of SaaS apps, maintaining consistent visibility and retaining the ability to manage all deployments at all times can prove to be a challenge.
Learn more about A10’s SSL decryption solutions via Thunder SSLi and centralized management and actionable analytics so your company can simplify its management processes, apply uniform security policies and efficiently decrypt and examine all incoming traffic.
Seeing is believing.
Schedule a live demo today.