DDoS Attack on Dyn Reveals New Threat Actor Strategies

In the early hours of Oct. 21, many top consumer application services — including Spotify, Reddit, Github and Twitter — experienced partial or total disruption in parts of the U.S. east coast and south central regions. It was the result of yet another massive distributed denial of service (DDoS) attack, but this time against DNS provider Dyn, an Internet performance vendor.
“Starting at 11:10 UTC on October 21st-Friday 2016 we began monitoring and mitigating a DDoS attack against our Dyn Managed DNS infrastructure,” Dyn stated on their service page. “Some customers may experience increased DNS query latency and delayed zone propagation during this time. Updates will be posted as information becomes available.”
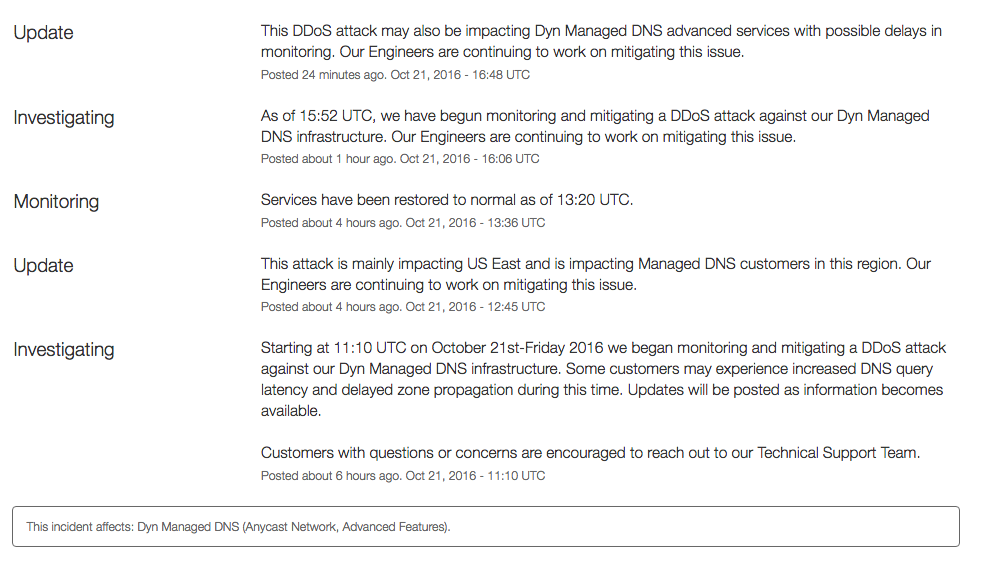
Shown in the screen above, Dyn was quick to identify, investigate, update and mostly resolve the DDoS attack against their managed DNS service, but some services were still affected Friday afternoon.
We are continuing to mitigate a DDoS against our Managed DNS network. For more information visit our status page.
— Dyn (@Dyn) October 21, 2016
This case is unique in the fact that the threat actors didn’t target individual organizations or services, but rather the virtual infrastructure that makes many of these application services possible.
“They’re innovating. This is a new spin on an old attack, as the bad guys are finding new and innovative ways to cause further discontent,” said A10 Networks Director of Cyber Operations Dr. Chase Cunningham. “It was an interesting point to see that the bad guys are moving upstream for DDoS attacks on the DNS providers, instead of just against sites or applications.”
The responsible criminal party was unknown at the time of posting. Details about the scale or scope of the DDoS attack have not been released, but Reuters reported that it was being investigated as a “criminal act.”
BREAKING: U.S. government probing whether east coast internet attack was a ‘criminal act’ – official
— Reuters Top News (@Reuters) October 21, 2016
DDoS bigger, faster and now with ransom
In September, security journalist Brian Krebs and European Web hoster OVH were hit with record DDoS attacks that leveraged IoT-based botnets to eclipse 600 Gbps and 1 Tbps, respectively.
“Threat actors are leveraging unsecure IoT devices to launch some of history’s largest DDoS attacks,” said Cunningham. “The immediate solution is for manufacturers to eliminate the use of default or easy passwords to access and manage smart or connected devices. Consumer adoption will be tricky, but this change is critical for the greater security of all. This will hinder many of the global botnets that are created and deployed for malicious use.”
On the Web Hosting Talk forum, Krebs found that some service providers are also being threatened with ransom notes, which claim attacks larger than 700 Gbps will be launched against the company if a Bitcoin ransom is not paid. There doesn’t appear to be a link between the two attacks. Here’s an excerpt of the threat:
“If you will not pay in time, DDoS attack will start, your web-services will go down permanently. After that, price to stop will be increased to 5 BTC with further increment of 5 BTC for every day of attack.
NOTE, i?m not joking. My attack are extremely powerful now – now average 700-800Gbps, sometimes over 1 Tbps per second. It will pass any remote protections, no current protection systems can help.”
How to stop large DDoS attacks
In some cases, the threat actor is correct. Most standard DDoS protection and mitigation solutions are limited in the capacity they can absorb.
That said, there are some DDoS mitigation best practices to prevent massive multi-vector DDoS attacks from taking a service or organization offline.
- Carefully balance resources, budget, technology, integration and vendor expertise. What applies to one organization (e.g., Web giant or service provider) certainly doesn’t work for another (e.g., SMB, mid-market organization or small retailer).
- Customize and integrate the DDoS protection solution to meet the specific needs of your organization. Understand your network and physical footprints, plus the hard costs of downtime relative to the expense of the DDoS strategy in question.
- Leverage a hybrid DDoS defense strategy that offloads traffic to a third-party cloud service once capacity hits a certain threshold. This is a cost-effective model for smaller organizations that are being proactive about DDoS security but can’t spend to defend worst-case scenario situations.
- For larger organizations like Web giants, service providers and global enterprises, invest in proven hardware with massive throughput capabilities. For example, the latest A10 Thunder TPS (14045) offering can handle DDoS attacks up to 300 Gbps with a single application; this solution can scale to 2.4 Tbps when deployed in cluster.
Seeing is believing.
Schedule a live demo today.