DOJ Charges Six for DDoS-for-hire Services, Kills 48 Sites

The Websites Hosted “Booter” or “Stresser” Services
On December 14th, the Department of Justice (DOJ) took control of 48 websites providing “booter” or “stresser” services, which let users launch destructive DDoS attacks cheaply and easily. Six Americans were charged with computer-related offenses for allegedly running the popular DDoS-for-hire services.
Law enforcement agencies globally are working together in Operation Power OFF to take down criminal DDoS-for-hire networks and punish their administrators and users.
The DOJ stated the 48 domains they confiscated assisted the customers of DDoS-for-hire platforms in launching massive amounts of DDoS attacks, capable of disabling websites and entire network service providers. A full list of the sites are below and as of this writing, several of these sites are still online.
Booter services and stresser services are advertised on the Dark Web, chat platforms, and Youtube. Payment is accepted through PayPal, Google Wallet, and crypto, with subscription costs varying from a few dollars to hundreds monthly. Prices depend on attack traffic, duration, and amount of concurrent attacks.
What is a DDoS-for-hire service? It’s a DDoS attack service that allows anyone to purchase and perform a distributed denial-of-service attack (DDoS attack) for a few dollars. These services are inspired by the software as a service (SaaS) business model, which is profitable because it allows the owner of a IoT botnet to perform the low-overhead attack.
Those Charged with the Cybercrimes
- Jeremiah Sam Evans Miller, also known as “John the Dev,” a 23-year-old from San Antonio, is the creator of supremesecurityteam[.]com and royalstresser[.]com. Miller has been charged with conspiracy and Computer Fraud and Abuse Act (CFAA) violations. The complaint alleges Royal Stresser launched near 200,000 DDoS attacks from Nov 2021 to Feb 2022 via their “fully anonymous” services.
Royal Stresser website before it was shut down by the DOJ
- Joshua Laing, a 32-year-old man from Liverpool, NY, has been charged with multiple CFAA violations related to his alleged involvement in a booter service called TrueSecurityServices[.]io. According to prosecutors, TrueSecurityServices[.]io had a user base of 18,000 between 2018 and 2022 and allegedly conducted over 1.2 million attacks.
- Corey Palmer, 22 of Lauderhill, FL, and Shamar Shattock, 19 of Margate, FL, were charged with conspiracy for ownership and operation, respectively, of booter.sx and astrostress.com. The latter had 30K users and 700K attacks.
- Angel Manuel Colon Jr., a 37-year-old from Belleview, Fla., is charged with managing the SecurityTeam stresser service, which allegedly conducted 1.3 million DDoS attacks from 2018-2022 and had 50,000 users. He was charged with conspiracy and CFAA violations.
- John M. Dobbs, 32, of Honolulu, HI was helping with breaking the CFAA through IPStresser[.]com. The site operated for 13 years until last month, generating 30 million DDoS attacks and gaining 2 million users.
DDoS-for-hire service owners claim no responsibility
Stresser providers and booter providers claim they have no control over how their services are used, and that they’re not breaking the law since their tools can be used for good or bad. Their sites contain Terms of Use that customers must agree to, wherein they only stress-test their own networks and not DDoS attack others. IPStresser’s admin, Dobbs, mentioned in an interview that customers must sign a digital signature to confirm they won’t use it for illegal activities, thus making him immune from liability.
The DOJ states that these disclaimers usually overlook the fact that most booter services heavily depend on continuously scanning the web to gain access to improperly set up gadgets, which are key to maximizing the intensity and effect of DDoS-for-hire assaults.
“Some sites use the term ‘stresser’ in an effort to suggest that the service could be used to test the resilience of one’s own infrastructure; however, as described below, I believe this is a façade and that these services exist to conduct DDoS attacks on victim computers not controlled by the attacker, and without the authorization of the victim,” reads an affidavit by FBI Special Agent Elliott Peterson out of the Alaska field office.
A complete list of FBI-seized “booter” or “stresser” domains
anonboot[.]com, api-sky[.]xyz, astrostress[.]com, booter[.]sx, booter[.]vip, brrsecurity[.]org, buuter[.]cc, cyberstress[.]us, dragonstresser[.]com, dreams-stresser[.]io, freestresser[.]so, instant-stresser[.]com, ipstress[.]org, ipstress[.]vip, ipstresser[.]wtf, orphicsecurityteam[.]com, ovhstresser[.]com, quantum-stresser[.]net, redstresser[.]cc, royalstresser[.]com, silentstress[.]net, stresser[.]app, stresser[.]best, stresser[.]gg, stresser[.]is, stresser[.]net/stresser[.]org, stresser[.]one, stresser[.]so, stresser[.]top, supremesecurityteam[.]com, truesecurityservices[.]io, vdos-s[.]co, zerostresser[.]com, ipstresser[.]xyz, kraysec[.]com, securityteam[.]io, blackstresser[.]net, ipstresser[.]com, ipstresser[.]us, stresser[.]shop, exotic-booter[.]com, mcstorm[.]io, nightmarestresser[.]com, shock-stresser[.]com, stresserai[.]com, sunstresser[.]com, bootyou[.]net, defconpro[.]net
More about DDoS-for-hire
Loyalty programs
As the DDoS-for-hire racket evolves, some such services have started offering repeat customers points and discounts toward future purchases. It’s a sort of DDoS loyalty program.
Some developers even offer bonus points for each attack conducted using their service. In other words, cybercriminals have their own loyalty and customer service programs. Most DDoS attacks are ordered through full-fledged Web services, which removes the need for direct contact between the two parties.
Customers use these Web services to register for an account, make payments, manage their balance and attack budget, access reports and more. They’re kinda of like Web services offered by legal services. In the DDoS-for-hire biz, many of these Web services boast thousands to hundreds of thousands of registered users.
IoT-based DDoS attacks are cheaper
The cost of a DDoS attack fluctuates based on the target, the duration of the attack and the geographic location of the target. According to The Register, a DDoS attack can cost anywhere from $5 for a 300-second attack to $400 for 24 hours, and the average price for an attack is around $25 per hour.
The price of a DDoS attack also takes into consideration the attack’s generation and the source of attack traffic. For example, an attack leveraging a botnet made up of Internet of Things (IoT) devices costs less than an attack that uses a botnet made up of servers.
Cybercriminals persistently look for more affordable means to set up botnets. The Internet of Things (IoT) benefits them in this. One of the current trends is the use of IoT zombie gadgets, like CCTV cameras, DVR-systems, and smart appliances, in DDoS attacks. As long as there are vulnerable IoT devices, criminals will keep taking advantage of them.
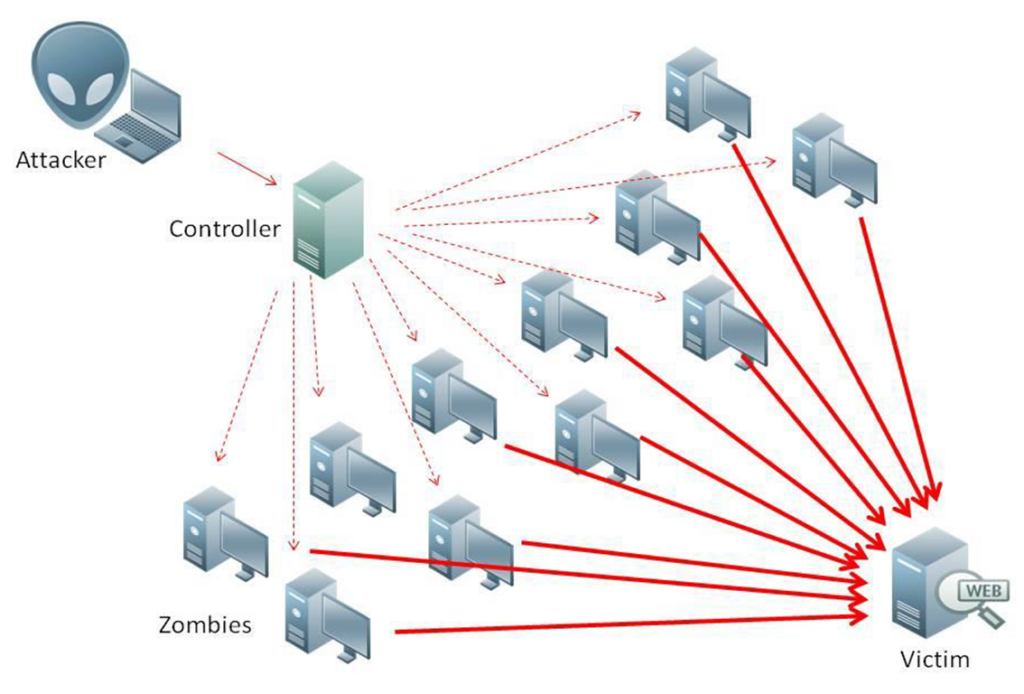
“DDoS attack man in the middle” by Nasanbuyn is licensed under CC BY 4.0
Dawn of the DDoS of Things
The rise of DDoS-for-hire services comes on the heels of a spate of high-profile DDoS attacks that reached unprecedented volume, size and scope. For the first time on record, DDoS attacks have exceeded 46 million rps, an upward swing that is expected to continue.
One of the botnets powering this tsunami of DDoS attacks is the Mirai malware, which takes advantage of unsecured IoT devices to build massive botnets and launch mammoth DDoS attacks. The uptick in DDoS activity has ushered in the DDoS of Things (DoT) era, where threat actors use unsecured IoT devices to build the botnets that drive colossal DDoS attacks.
How does A10 Networks fight DDoS attacks and DDoS-for-hire services?
Thunder® Threat Protection System (TPS®), a line of high-performance DDoS protection solutions, detects and mitigates volumetric, multi-vector DDoS attacks at the network edge. For service providers, enterprises and security-conscious businesses, Thunder TPS is the first line of defense for network infrastructure. It helps prevent IoT-powered DDoS attacks and protects your business from the DDoS of Things.
Related Resources
- Testing DDoS Defense Effectiveness at 300 Gbps Scale and Beyond (White Paper)
- BR.Digital Grows Business with Automated DDoS Detection (Case Study)
- Dodging and Defeating DDoS Attacks: Data Center Provider Guide (eBook)
- The Rise of Botnet and DDoS Attacks (Blog Post)
- Five Most Famous DDoS Attacks and Then Some (Blog Post)