DDoS Attack Prevention and DDoS Protection Best Practices
Stopping Infrastructure Attacks and Application Attacks with DDoS Tools and Threat Intelligence
Easy to launch and often devastatingly effective, a distributed denial of service (DDoS) attack is one of the most common threats in today’s cybersecurity landscape. In simple terms, a DDoS attack seeks to disrupt a target’s connectivity or user services by flooding its network with an overwhelming volume of fraudulent traffic, typically through a botnet. The motivation behind the attack can vary from political protests, cyberwarfare, illicit competitive advantage, or extortion to undermining the victim’s security stack as a cover for data theft. In some cases, ransomware gangs even launch DDoS attacks against their victims to increase the pressure for payment. Knowing how to stop a DDoS attack is a critical priority for cybersecurity professionals.
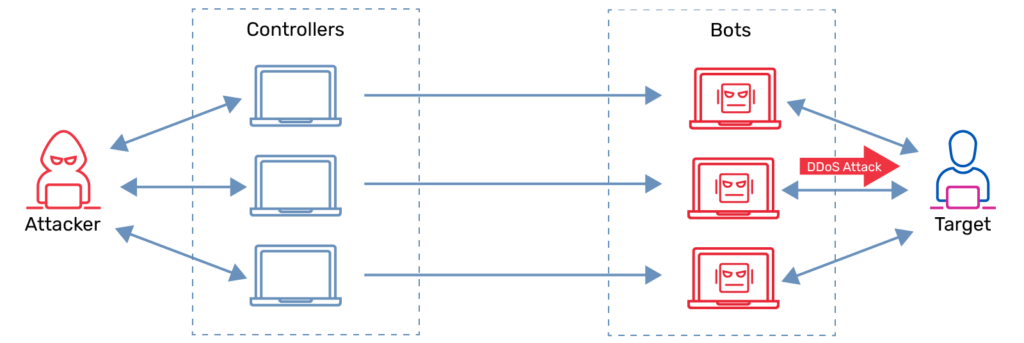
The DDoS attack disrupts a target’s connectivity by inundating its network with massive amounts of fraudulent traffic, mainly via a botnet
The damage from a DDoS attack can be devastating. In one recent survey, 98 percent of respondents reported costs of more than $100,000 for each hour of downtime, while over one-third estimated costs in excess of $1 million. The average DDoS attack causes $218,000 in direct damage, in addition to any accompanying extortion, data theft, business disruption, or harm to the victim’s reputation and business and customer relationships. Famous DDoS attacks in recent years, including multi-terabit attacks on Google, AWS, and GitHub, show the potential scale of the threat.
Without an effective DDoS attack prevention strategy, complemented with DDoS protection solutions and threat intelligence, organizations are at significant risk.
Denial of Service Attack Types: Infrastructure Attacks and Application Attacks
At a high level, a denial of service attack can fall into two categories according to the level of the OSI model at which it functions.
Infrastructure attacks target vulnerabilities or weaknesses in OSI Layer 3 (network) or Layer 4 (transport). Most DDoS attacks fall into this category, including SYN flood, Ping of Death (PoD), ICMP flood, and UDP flood attacks. Depending on the specific tactics used, infrastructure attacks can be further subdivided into volumetric attacks and protocol attacks.
Volumetric attacks, the most common type of denial of service attack, focus on flooding the victim’s server or bandwidth with false requests to render it unable to accept regular traffic. Protocol attacks target the protocols used in transferring data to crash a system.
Application attacks work at OSI Layer 7 (application) to target weaknesses in a specific application to render it unable to communicate or deliver content. This most often occurs through the HTTP protocol, and less commonly using FTP, NTP, SMTP, or DNS. Unlike volumetric infrastructure attacks, application attacks can achieve their intended impact with a relatively low volume of requests, making them particularly difficult to detect.
How to Stop a DDoS Attack: 5 Best Practices for DDoS Attack Prevention
To reduce the risk of a devastating denial of service attack, organizations need to leverage comprehensive measures including network traffic baselining and monitoring, DDoS attack planning, DDoS attack mitigation measures, and the deployment of DDoS protection tools and threat intelligence. The following best practices can form the foundation of an effective DDoS attack prevention strategy.
1. Know What to Watch for—and Watch for It
To detect a DDoS attack underway before it’s too late, you need to know what normal network traffic looks like. By creating a baseline of your usual traffic pattern, you can more easily identify the symptoms of a DDoS attack, such as inexplicably slow network performance, spotty connectivity, intermittent web crashes, unusual traffic sources, or a surge of spam.
Vigilant monitoring is critical, including both network and application traffic; even a small anomaly can signal a test by cybercriminals in advance of a larger attack. The sooner you detect an event in progress, the more quickly and effectively you can put DDoS attack mitigation plans into action. At the same time, it’s critical to minimize false positives in order to avoid unnecessary operational disruptions.
2. Make a Denial of Service Response Plan
When you’ve determined that a likely DDoS attack is underway, your organization needs to be able to respond quickly and efficiently. Detailed planning will avoid the need to improvise under pressure. Your plan should include:
- A checklist of systems, assets, and advanced threat detection tools
- A defined response team with the DDoS attack mitigation competencies
- Procedures to maintain business operations for the duration of the attack
- Protocols for incident notification and escalation
- A communications plan covering both employees and external stakeholders such as customers and partners and the media
3. Ensure a Resilient Infrastructure
Given the high likelihood of an attempted DDoS attack at some point, you should take steps to minimize the impact of a successful denial of service. Designing your network and systems to accommodate excess traffic—from 2 – 5X your anticipated baseline need—can help you absorb an attack long enough to mount a response. Distributing resources can limit the reach of an attack, such as by putting servers in different data centers, and putting data centers on different networks and in different physical locations. Redundant devices and high-availability architecture can speed system restoration following a DDoS attack (note that they should be launched only after an attack has concluded to avoid exposing them to an ongoing attack). Avoid or harden bottlenecks and single points of failure that can be especially vulnerable to a traffic flood.
4. Take Refuge in the Cloud
The cloud offers a few possibilities to reduce the risk of a DDoS attack. Migrating assets to the cloud is one approach; cloud providers have far more bandwidth than the typical enterprise, and the distributed nature of the cloud can aid resiliency. If one server is crashed by a DDoS attack, others will continue operating; similarly, secure data backups in the cloud can aid rapid recovery in the event of system corruption.
On the other hand, multi-tenant cloud environments can bring risks of their own. A cloud, hosting, or colocation provider who detects a DDoS attack on one customer might shut down all their traffic in order to prevent spillover impacts on other customers, leaving the company unable to make a more surgical response to preserve some services.
By the same token, an attack on another cloud provider customer might impact your company even if you’re not the original target. In this light, it’s important to work with cloud, hosting, and colocation providers who offer DDoS protection as a service for their customers.
5. Deploy DDoS Protection Solutions and Threat Intelligence
DDoS attack prevention depends on a multilayered strategy of best practices, tools, and threat intelligence. Your anti-DDoS solution should include capabilities for traffic monitoring, real-time threat detection, anomalous behavior blocking, zero-day attack pattern recognition, DDoS scrubbing, and automated response. Threat intelligence is essential to enrich your DDoS tools with timely data about current DDoS activity and trends, including the IP addresses of DDoS botnets and vulnerable servers known to be associated with DDoS attacks. Leveraged in conjunction with real-time threat detection, artificial intelligence (AI)/machine learning (ML) capabilities, and automated signature extraction, threat intelligence enables organizations to take a proactive approach to DDoS attack mitigation.
How A10 Networks Powers DDoS Attack Prevention
Top service providers, enterprises, online gaming companies, and other organizations depend on A10 Networks to reduce the risk of a denial of service attack. A10 Networks Thunder® TPS provides scalable and automated DDoS protection powered by advanced machine learning to detect and mitigate attacks. A10 Networks DDoS threat intelligence leverages reputation data from over three-dozen security intelligence sources to instantly assess and block traffic from millions of known DDoS weapons. The definitive annual DDoS Threat Report provides vital insight for security leaders to proactively improve DDoS defenses.
Related DDoS Attack Prevention Resources
- The Best DDoS Protection Services for Data Center Providers (Webinar)
- BR.Digital Grows Business with Automated DDoS Detection (Case Study)
- How Effective is your DDoS Protection? (Report)
- Dodging and Defeating DDoS Attacks: Data Center Provider Guide (eBook)
- Digital Divide: Protecting the Unconnected from DDoS Attacks (Webinar)