Carpet-bombing Attacks Highlight the Need for Intelligent and Automated DDoS Protection

Recently a large service provider in Eastern Europe contacted the A10 threat research team for insight into a series of DDoS attacks against its network. While the attacks were not service impacting, the frequency and persistence of the attacks raised internal concerns that the attacks might mask a more malicious intent: could this be a state actor planting malware or testing their defenses for a larger attack against critical infrastructure? Were they the only one being attacked, or was it all service providers in the region?
This is not an unreasonable concern. With the Ukraine conflict on-going, DDoS attacks are a favorite weapon to supplement on-the-ground conflict. The A10 threat research team had observed DDoS attacks against Ukraine early in the conflict and they are continuing.
The service provider had a security team that could see the endpoint of the attack – the impact on their network – the size and duration of each attack, the volume of traffic generated, and which network elements and ports were being impacted and how close to traffic load thresholds were being reached. What they could not see was the attack’s origination and the broader context of these attacks against any others in the region or the world.
Our research team could see the attacks in the A10 Defend Threat Control portal, the example screen shot is below. So, what insights was the threat control portal able to provide to the service provider team?
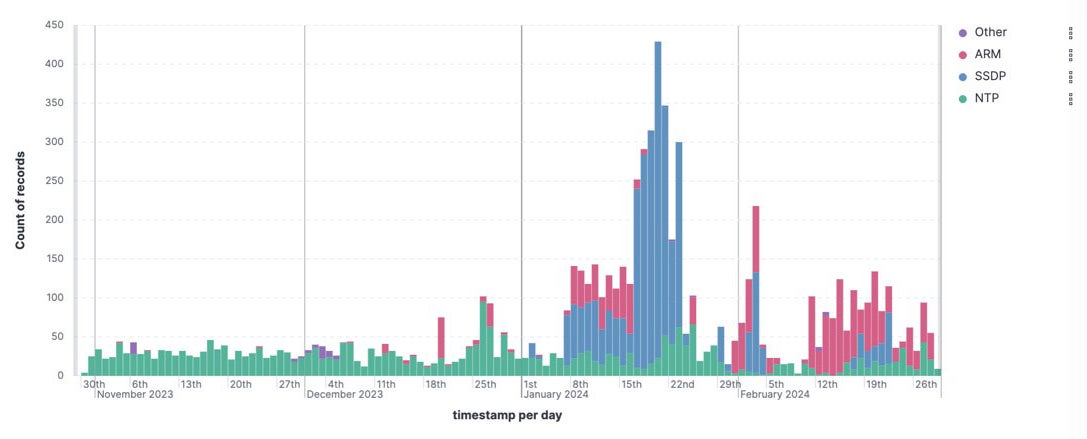
Figure 1. SSDP DDoS attacks against Eastern European service provider observed in A10 Defend Threat Control
What it is and What it is Not
The attacks were carpet-bombing attacks using SSDP and were targeting every IP address range in the service provider organization ASNs.
Carpet-bombing attacks are not new, but they have become increasingly popular in recent years. Named after WWII style bombing of entire cities, carpet-bombing attacks do not focus on individual targets, but instead spread malicious traffic across a broad range of IP addresses, often an entire CIDR or multiple ASNs. While the DDoS traffic volume on an individual IP address can be small, collectively, the traffic volume can be quite large. Traditional defense used by service providers detect DDoS traffic by a small range of IPs or network elements with established detection thresholds (packets per second or Mbps). Since a carpet-bombing attack uses a small level of traffic per IP or host, it never triggers the DDoS defenses of those elements. For example, a 200 Gbps attack focused on a single IP address would be detected and mitigated quickly by most DDoS protection systems. If spread out over 2,000 host targets simultaneously, the same attack volume would result in each host receiving 12.5 mbps of traffic, avoiding detection and flying under the radar of most service providers. This could possibly degrade service if not actually causing an outage, although, the same volume of traffic is generated.
Who Would Launch a Carpet-bombing Attack?
With the ready availability of DDoS-for-hire tools on the dark web and over 15M DDoS weapons available globally, just about anyone can launch a DDoS attack anywhere, with minimal skills and investment. However, carpet-bombing attacks are sophisticated and require launching attacks against potentially thousands of hosts (IP addresses). Dark web DDoS services are priced on the number of targets, size of the attack (Gbps or PPS) and duration. Amateur cyber criminals, such as gamers, might invest in very short duration attacks to kick specific opponents offline and gain an advantage, but are unlikely to be interested in paying the premium rates for longer-term and broader attacks. Longer duration attacks are more likely launched by a more sophisticated and well-funded adversary, which could include a state actor.
Why have Carpet-bombing Techniques Become so Popular?
There are several reasons that this technique might be used:
- The broad range of targets can hide the real, intended target, ideal for more covert crimes.
- Carpet-bombing can be combined with reflection-amplification techniques to maximize their distribution and traffic volume.
- Carpet-bombing DDoS attacks can be quite difficult to detect and mitigate.
- Carpet bombing can be more effective – and damaging – than traditional DDoS attack methods.
Carpet bombing is one of several techniques that make it harder to identify the target and the source. For example, a reflection-amplification attack is a commonly used technique that typically exploits vulnerabilities in internet servers to amplify the attack traffic, making it harder to identify the true source. A carpet-bombing attack spreads attack destinations to a wide range of IP addresses, making it harder to identify the target and generating an unmanageable number of alerts. Sometimes these techniques can be combined.
ISPs are Especially Vulnerable to Carpet Bombing
Service providers, like the one described here, carry massive amounts of traffic over their networks. Their DDoS defenses are usually designed around detecting traffic anomalies and spikes that could disrupt or impair network availability and responsiveness. This is usually done by establishing traffic thresholds that when exceeded, trigger a defense response. Carpet-bombing attacks are successful because they disperse malicious traffic across thousands of IP addresses. Thus, any single IP is targeted with a small volume of traffic that flies under the radar of the detection system. Also, multiple applications and systems within the service provider network would be targeted simultaneously. This means that the service provider may need to correlate the data from multiple systems to see the full magnitude of the attack and manage alerts from different systems. Cyber criminals also apply automation techniques to change the target IP addresses at will. Proper defense requires a level of automation and sophisticated detection that is missing in many organizations’ existing DDoS protection systems.
ISPs can get a head start against carpet-bombing attacks through intelligent threat data and modern DDoS detection and mitigation. With accurate data, malicious IPs, hosts, and servers can be identified upfront and blocked from gaining access into the network. Then appropriate DDoS defenses can be initiated using machine learning and AI-based detection and surgical mitigation so that legitimate traffic can still be carried.
A10 Defend Suite
Modern DDoS attacks have evolved far beyond simple volumetric flooding. They are now sophisticated, multi-layered, and often leverage several techniques to evade detection. The A10 Defend suite, consisting of A10 Defend Detector, Mitigator, Orchestrator, and Threat Control, helps organizations enable more effective DDoS protection and/or create profitable DDoS scrubbing services for their customers. A10 Defend Detector has multiple detection mechanisms and can precisely detect such complex targeted volumetric attacks.
A10 Defend provides a holistic DDoS protection solution that is scalable, economical, precise, and intelligent to help customers ensure optimal user and subscriber experiences. Used by top service providers, enterprise, cloud, and online gaming companies, the A10 Defend suite consists of four major components:
- A10 Defend Detector efficiently identifies abnormal traffic
- A10 Defend Mitigator automatically and intelligently mitigates the identified inbound DDoS attack
- A10 Defend Threat Control proactively provides standalone layered defense and actionable insights
- A10 Defend Orchestrator provides a centralized point of control for seamless DDoS defense execution
The A10 Defend Threat Control portal provides a real-time snapshot into DDoS attacks globally and provides a view of the complexity in protecting against frequent and diverse DDoS attacks.