Bart Ransomware: How SSL Inspection Stops the New Attack

A new ransomware strain is showcasing the adaptability of threat actors. Nicknamed Bart, this new advanced attack downloads malware to end-user machines over HTTPS, but varies from predecessors like Dridex 220 and Locky Affid=3. The Bart ransomware doesn’t require connection to a command-and-control server to encrypt files.
Instead, it uses an intermediary loader to download both the ransomware and a ransom note directly to the endpoint. The Bart ransomware was expertly investigated and dissected by researchers at Proofpoint. (Bonus points for their Simpsons-inspired chalkboard).
Thankfully, proper SSL decryption and inspection helps defeat this malware and secure your business via two methods.
Mitigation 1: Decrypting Email
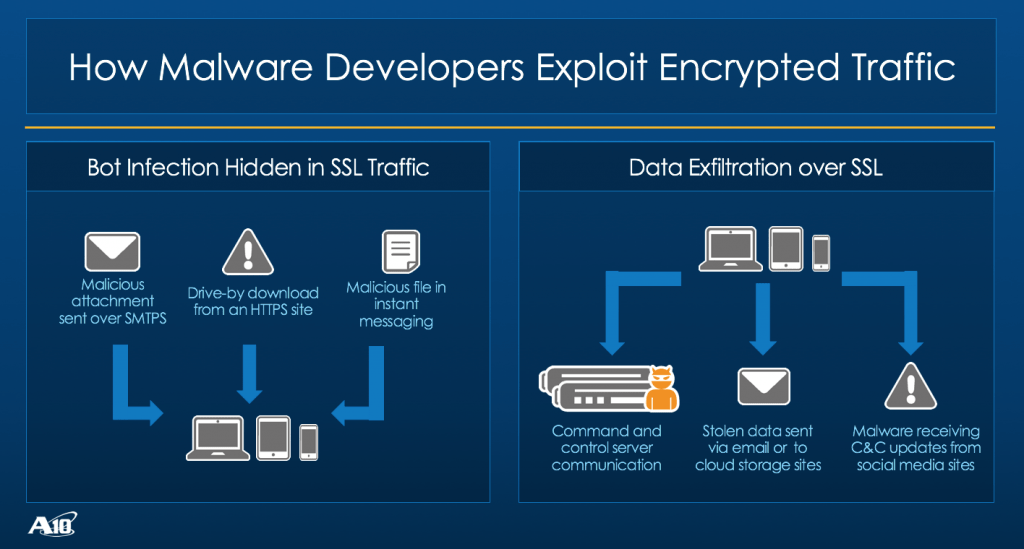
According to Proofpoint, the Bart payload is delivered over HTTPS when a target clicks on a malicious attachment in an email. Threat actors are able to evade detection from perimeter security controls by encrypting the email and accompanying attachments.
For public email services (e.g., Gmail, Yahoo, etc.), this is achieved through SSL-based encryption. For enterprise-grade email clients (e.g., Microsoft Outlook), the attachments are often encrypted with the S/MIME-based standard. Proper SSL (Secure Sockets Layer) decryption and SSL inspection can properly monitor these specific attack vectors and allow perimeter security tools to take necessary actions.
Public Email
If the phishing attempt is sent to a public email domain, the malicious attachment will likely evade detection by hiding behind SSL encryption.
With a proper SSL decryption solution in place — coupled with integrated third-party security controls — organizations are able to quickly decrypt, inspect and block malicious traffic. The remaining “good” traffic is then re-encrypted and sent on its way without hindering performance.
This helps organizations protect valuable data and assets, even when employees are accessing personal cloud-based email — and the potential for increased exposure to phishing attempts — that is encrypted.
Corporate Email
In a more common enterprise scenario, a threat actor sends phishing attempts to a large number of corporate email addresses in hopes that a few end-users are fooled into clicking and executing dangerous files. Malware would then covertly download ransomware from a malicious site by hiding itself from corporate security systems behind SSL encryption.
The nefarious activity typically identified and blocked by a network forensics sensor or intrusion detection or prevention systems (IDS/IPS) can’t detect the attack without first decrypting the communications.
A proven SSL decryption solution will have authorized access to the certificate key and will have the ability to securely decrypt and re-encrypt network traffic for secure SSL inspection by the security infrastructure.
Mitigation 2: Stop the Download
As mentioned, where Bart differs from previous ransomware variants is the lack of a command-and-control requirement. This makes executing a successful ransomware attack that much easier and quicker for threat actors.
Without the need to call back to a command-and-control server, there’s less of a chance of being discovered by security solutions like network behavior anomaly detection (NBAD) or next-generation firewall (NGFW) solutions.
Proper SSL decryption would either expose the attachment so that the initial payload would be stopped (assuming it’s not a zero-day vulnerability), or the outbound connection and subsequent download of the ransomware payload would be blocked.
High-Performance SSL Decryption is Possible
For security-conscious organizations committed to proper and proactive cybersecurity, SSL decryption and SSL inspection is no longer a luxury. It’s a critical security requirement.
SSL-encrypted traffic is growing, rendering most security devices ineffective. According to a 2016 Ponemon Institute report, 80 percent of responding organizations were a victim of a cyber attack or malicious insider. Of those, 41 percent of the attacks used encryption to evade detection.
When evaluating SSL decryption solutions, consider:
- Dynamic URL classification to define policies that allow specific traffic streams to bypass decryption (e.g., for PCI or HIPAA compliance)
- Proper URL filtering to deny access to specific URL categories or harmful sites
- Use of advanced server load balancing to offload decryption and improve performance
- Traffic-steering to intelligently route traffic, optimize performance and reduce security appliance costs
- Validated interoperability with leading solutions (e.g., Cisco FirePOWER, FireEye, RSA, IBM, etc.)
Seeing is believing.
Schedule a live demo today.