Application Security in the Cloud: Who’s Responsible?

This is a recap of a talk I gave at Cisco’s DevNet Create, a developer conference held last month in San Francisco.
We’ve all heard about the benefits of cloud infrastructure: improved productivity, cost savings, efficiency, agility and a host of other buzzwords that paint cloud as the be all, end all for IT.
Most organizations today either already run workloads in the cloud or plan to experiment with cloud in the very near future. And it’s up to businesses to decide whether they choose cloud infrastructure provided by public cloud providers like AWS, Microsoft Azure and Google Cloud Platform, or cloud infrastructure maintained by their organization’s IT team.
In compliance heavy businesses, such as financial institutions, a new trend has emerged: organizations are running an isolated virtual private environment on public cloud infrastructure.
Securing the App
No matter where an application is hosted, securing the application delivery remains the primary concern. And it’s security that is causing a great deal of confusion in the industry. It raises the question: who owns application security in the cloud? Is it the cloud service provider or application teams?
Some believe that applications are secure simply because they’re deployed in the cloud, which would make application security the sole responsibility of the cloud infrastructure provider.
Others feel that security is the responsibility of the application owners – and as such, applications should not be deployed in the cloud due to security risks or unless security is properly baked in.
Blurred Lines
It is well documented by public cloud providers like AWS and Azure that application security is a shared responsibility between the cloud infrastructure providers and the application owners. However, the lines are blurred and the division of ownership is not clearly defined.
Applications deployed in cloud infrastructure are accessed via the network. In this case, viewing the security responsibility from the network infrastructure point of view makes more sense.
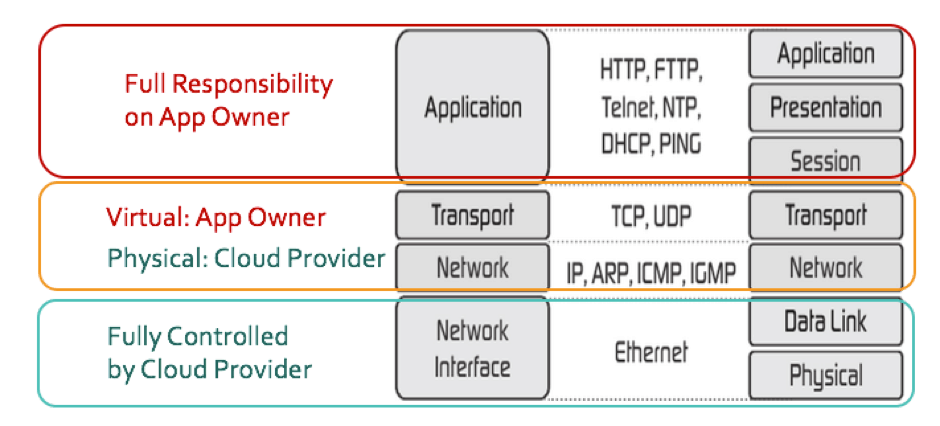
This chart shows the division of ownership between cloud providers and app owners.
In this example, the cloud providers control and manage the physical infrastructure resources, hence it’s their job to make sure the application that runs on that infrastructure is secure.
However, with virtual and software-defined networks (SDNs), application owners define the virtual networks as per application architecture, referred to infrastructure as code. Thus virtual network security resides with the application owners. Traditionally, application owners have an established set of best practices, and setting up network security is a no-brainer. Because the network is part of the infrastructure, cloud providers will provide tools for virtual network security and also for the implementation.
Cloud providers, however, have no visibility into what happens at the application layer and have no way to help the application owners in this area. The application security layer is the responsibility of application owners.
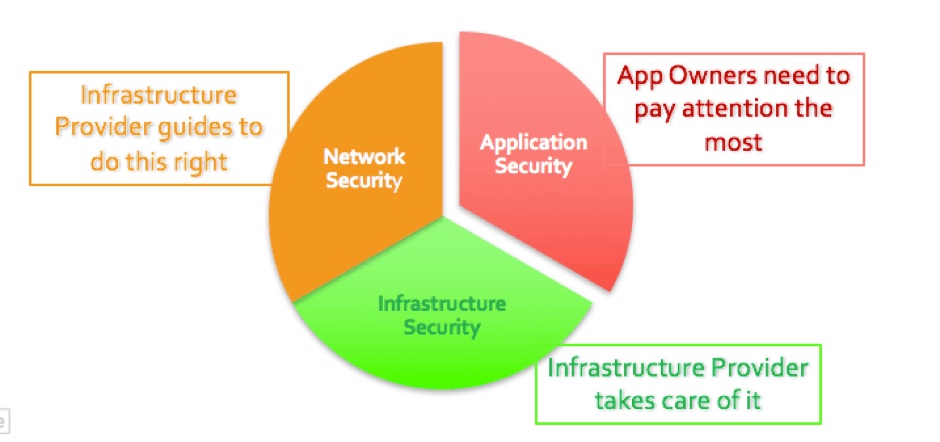
This chart shows which part of security falls to whom
Application Security Challenges in the Cloud
Before we can evaluate a solution for application security, we need to understand the following challenges:
- Security Monitoring – there are numerous questions about the solution’s capability, but monitoring the security should not be one of them. Security monitoring is imperative; it’s a must-have.
- Application Vulnerabilities – these are susceptible to attackers looking to exploit and attack an application, either to gain complete control over it, deform it or steal data. OWASP analyzes such vulnerabilities and exploits, and regularly publishes a list of its top 10 identified vulnerabilities.
- Malware and Ransomware – another well-known security problem that impacts a lot of users and should be addressed prior to deploying an application in the cloud.
- BOTs – approximately 30 percent of traffic comes from non-useful BOTs (i.e. bad BOTs). While some people don’t consider them a security issue, yet, bad BOTs can wasted 30 percent in server resources, resulting in a huge loss of productivity.
- Application Layer DDoS Attacks (volumetric or protocol exploits) – are also a concern as DDoS attacks evolve in size, scope and sophistication. DDoS protection is a serious consideration for both application owners and cloud infrastructure providers.
Solving These Challenges
Fortunately, there are solutions available to overcome the security challenges associated with cloud applications.
Web Application Firewalls (WAFs), for example, can handle the common vulnerabilities listed by OWASP. And IP reputation and other signature databases have been created to combat malware and bad BOTs.
Many Application Delivery Controllers (ADCs) bundle application security solutions with load balancing and other key application services. Having a complete set of application delivery tools along with security and visibility in a DDoS resilient architecture can create a complicated deployment architecture. Consider a solution that unifies all aspects of the application traffic management, application security with traffic and security analytics into a single system and layers central management and control on top of it. This type of solution will alleviate most of your cloud application security concerns.
A10 Networks helps customers overcome cloud application security challenges with A10 Lightning ADC, a solution that unifies into a single system all aspects of application traffic management – from application security to per-application traffic and security analytics. And the A10 Harmony Controller provides customers centralized management and analytics for secure application services across any underlying infrastructure — from traditional on-premise data centers to public, private and hybrid clouds.
I would like to thank Cisco for the opportunity to present at their DevNet Create developer conference.
If you want to learn more, you can check out my full talk on Youtube and view my presentation on Slideshare.
Seeing is believing.
Schedule a live demo today.