2020 Was a Busy Year for DDoS Attacks

The latest State of DDoS Weapons Report Explores DDoS Weapons, DDoS Attacks and Malware Activity in the Second Half of 2020
2020 will go down in history as one of the most eventful years, and not just because of the coronavirus pandemic. Cybercriminals were very active throughout the year and leveraged the global pandemic to increase attacks, large and small, on vulnerable organizations including healthcare, education, and government, making 2020 one of the most active years for cybercriminals in general and for DDoS attacks in particular. It is also not surprising that we saw some of the largest DDoS attacks ever recorded in 2020 as well.
At A10 Networks, we have been tracking DDoS attacks, DDoS attack methods, and malware activity over the past several years and have observed a steady increase in the frequency, intensity, and sophistication of DDoS attacks. The second half of 2020 was no different and we saw some interesting developments in the world of DDoS.
The A10 Networks DDoS Attack Report summarizes specific DDoS and malware activity observed around the globe during the past six months.
In our last report we explored the use of malware in the recruitment of botnet devices, taking a closer look at the most frequent example, the Arm7 malware binary, which demonstrated its complexity via multi-layered attack techniques.
In this report, we took a closer look at how 200,000+ devices were compromised from virtually nothing at a sizeable cable broadband provider in India, the observed behavior of these devices, what exploits were used to hijack these devices and some recommended best practices to protect against potential attacks from these systems.
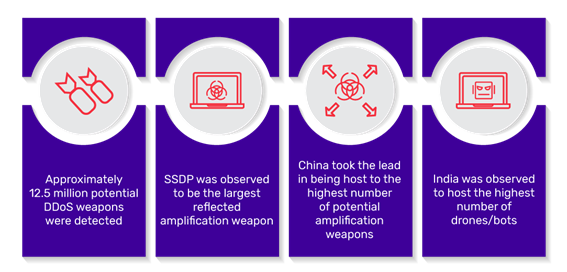
Some key insights from the report include: